Author:
Sara Rhodes
Date Of Creation:
9 February 2021
Update Date:
2 July 2024
Content
- Steps
- Method 1 of 4: How to Protect Your Accounts
- Method 2 of 4: How to keep your phone secure
- Method 3 of 4: How to protect your computer
- Method 4 of 4: How to Ensure Network Security
- Tips
- Warnings
It seems that in the modern world, anyone can become a victim of hacking. Every year, there are hundreds of successful cyberattacks and countless attempts. It will not be possible to completely protect against hacking, but you can always take preventive measures. Learn how to improve the security of your accounts, mobile devices, computers, and networks in this article.
Steps
Method 1 of 4: How to Protect Your Accounts
 1 Create complex passwords. Passwords to access accounts in applications or websites should be composed of combinations of numbers, upper and lower case letters, and special characters that are difficult to guess.
1 Create complex passwords. Passwords to access accounts in applications or websites should be composed of combinations of numbers, upper and lower case letters, and special characters that are difficult to guess. - Do not use one password for multiple sites or accounts. This will limit the damage caused by cracking one of the passwords.
 2 Use a password manager. Password managers store and automatically enter data when you log into sites, which allows you to create complex and unique passwords without having to worry about having to enter your password more than once. Of course, it is highly recommended to always keep track of passwords yourself, but a password manager will significantly secure mobile devices.
2 Use a password manager. Password managers store and automatically enter data when you log into sites, which allows you to create complex and unique passwords without having to worry about having to enter your password more than once. Of course, it is highly recommended to always keep track of passwords yourself, but a password manager will significantly secure mobile devices. - Highly rated third-party password managers include Dashlane 4, LastPass 4.0 Premium, 1Password, Sticky Password Premium, and LogMeOnce Ultimate.
- Most browsers have a built-in password manager that stores your data (but often unencrypted).
 3 Do not share your password with anyone. This is an obvious tip, but it should be repeated: never give site administrators the password to access your account, except for a number of school services.
3 Do not share your password with anyone. This is an obvious tip, but it should be repeated: never give site administrators the password to access your account, except for a number of school services. - The same rule applies to employees in the information technology industry, Microsoft or Apple.
- Also, do not share the PIN and passcode of your phone or tablet with anyone. Even friends can accidentally share your password with other people.
- If for some reason you need to share your password with another person, then change it as soon as possible after completing the required actions with your account.
 4 Change passwords often. In addition to confidentiality, you should also change your passwords for different accounts and devices at least every six months.
4 Change passwords often. In addition to confidentiality, you should also change your passwords for different accounts and devices at least every six months. - Do not use the same password twice (for example, your Facebook password must be different from your banking password).
- When changing the password, the changes must be substantial. It is not enough just to replace one letter or number.
 5 Use two-factor authentication. In this case, after entering the username and password, you also need to enter the code received in a text message or other service. This approach makes it harder for crackers even if they got your password.
5 Use two-factor authentication. In this case, after entering the username and password, you also need to enter the code received in a text message or other service. This approach makes it harder for crackers even if they got your password. - Many major sites, including popular social media sites, offer a variety of two-factor authentication options. Check your account settings and enable this feature.
- You can set up two-factor verification for your Google account.
- Popular alternative code services include Google Authenticator, Microsoft Authenticator, and Authy. Also some password managers have a similar function.
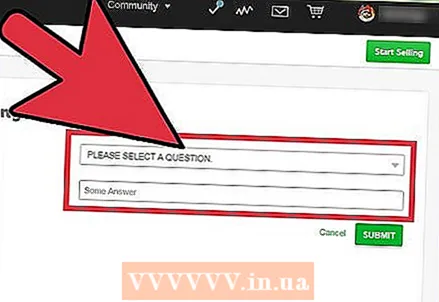 6 Don't use correct answers to security questions. When filling out the item of answers to security questions, you should not use the correct answers. Hackers can find out your mother's maiden name or the street where you lived as a child. On the contrary, it is better to give deliberately erroneous answers or even replace them with passwords without reference to the question itself.
6 Don't use correct answers to security questions. When filling out the item of answers to security questions, you should not use the correct answers. Hackers can find out your mother's maiden name or the street where you lived as a child. On the contrary, it is better to give deliberately erroneous answers or even replace them with passwords without reference to the question itself. - For example, to the question "What is your mother's maiden name?" you can think of an answer like "Pineapple".
- Better yet, use a combination of random numbers, letters, and symbols like "Ig690HT7 @".
- You can record your answers to security questions and store them in a safe place so you can restore your account in case you forget the answers.
- For example, to the question "What is your mother's maiden name?" you can think of an answer like "Pineapple".
 7 Please read the privacy policy terms carefully. Any company that receives your information must use a privacy policy that details how it will handle such information and the extent to which this information may be disclosed to others.
7 Please read the privacy policy terms carefully. Any company that receives your information must use a privacy policy that details how it will handle such information and the extent to which this information may be disclosed to others. - Most people never read these terms. The text can be cumbersome, but it's worth at least skimming the conditions with your eyes to know how your data will be used.
- If a certain point does not suit you or causes concern, then it is better to think about whether it is worth trusting your information to such a company.
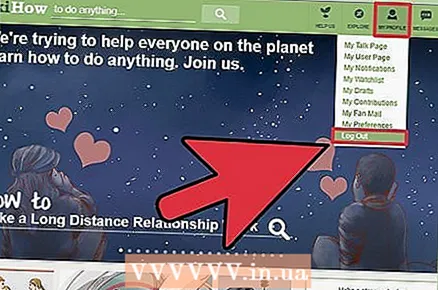 8 Sign out of your accounts after you finish working. Just closing the browser window is usually not enough, so always click on the account name and select End session or Sign out of your accountto manually log out of your account and delete your login information from this site.
8 Sign out of your accounts after you finish working. Just closing the browser window is usually not enough, so always click on the account name and select End session or Sign out of your accountto manually log out of your account and delete your login information from this site. 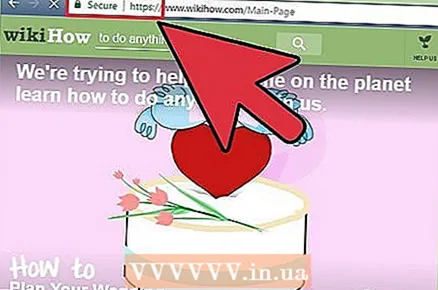 9 Make sure you are on the official website before entering your password. Phishing sites that disguise themselves as a login page on social networks or banking services are one of the easiest ways to get someone else's data. First of all, take a look at the site's URL: if it looks like a well-known site, but with a few differences (like “Facebok” instead of “Facebook”), then the site is fake.
9 Make sure you are on the official website before entering your password. Phishing sites that disguise themselves as a login page on social networks or banking services are one of the easiest ways to get someone else's data. First of all, take a look at the site's URL: if it looks like a well-known site, but with a few differences (like “Facebok” instead of “Facebook”), then the site is fake. - For example, only enter your Twitter login information on the official Twitter website. Do not include information on a page that requires such information for features like share an article or an image.
- Possible exception: university services can use existing services like Gmail on their home page.
Method 2 of 4: How to keep your phone secure
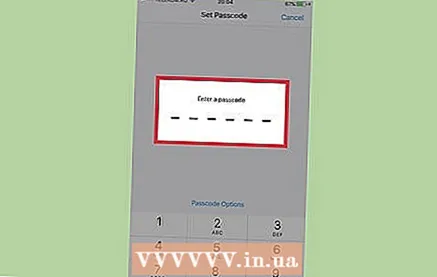 1 Change the access password frequently. The first line of defense against people who are trying to spy on or steal your data is a strong and constantly changing password to access your device.
1 Change the access password frequently. The first line of defense against people who are trying to spy on or steal your data is a strong and constantly changing password to access your device. - Make significant changes and do not limit yourself to replacing one or two characters.
- On most phones, you can set a "complex" password, which includes letters and symbols in addition to the usual numbers.
- Do not use Touch ID or other fingerprint access features. They may seem stronger than a password, but they are much easier to bypass because attackers can create a copy of your fingerprint using a printer.
 2 Keep your devices and software up to date. Install all updates as they are released. These can be updates to the Facebook application for your smartphone, or the entire operating system.
2 Keep your devices and software up to date. Install all updates as they are released. These can be updates to the Facebook application for your smartphone, or the entire operating system. - Many updates address security weaknesses and vulnerabilities. Failure to update software may expose your device to unwanted risk.
- Use the automatic app update feature to get rid of unnecessary problems.
 3 Charge your phone with a reliable USB port. These include the connectors on your computer and the charging ports in your car. Public USB ports in cafes or squares can put your data at risk.
3 Charge your phone with a reliable USB port. These include the connectors on your computer and the charging ports in your car. Public USB ports in cafes or squares can put your data at risk. - For this reason, it is recommended that you take the power plug with you when traveling.
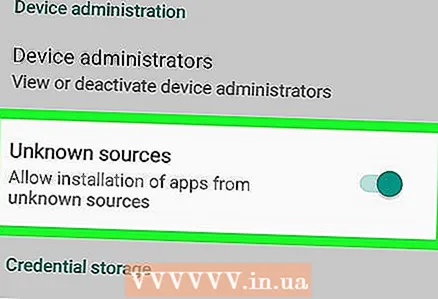 4 Do not unlock the bootloader for root access or download third-party applications. IPhones and Android devices have security measures that can be circumvented by actions such as unlocking and removing restrictions, but such actions will leave the smartphone vulnerable to viruses and hacks. Likewise, downloading applications from unverified sources (“third party applications”) increases the risk of malware being used on your device.
4 Do not unlock the bootloader for root access or download third-party applications. IPhones and Android devices have security measures that can be circumvented by actions such as unlocking and removing restrictions, but such actions will leave the smartphone vulnerable to viruses and hacks. Likewise, downloading applications from unverified sources (“third party applications”) increases the risk of malware being used on your device. - Android devices have a built-in security feature that prevents the installation of apps from unknown sources. If you have disabled such a function (tab Safety in the Settings menu), be careful when downloading applications from various sites.
Method 3 of 4: How to protect your computer
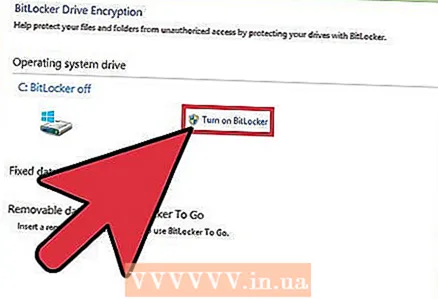 1 Encrypt data on your hard drive. If the data on the hard drive is encrypted, then the hacker will not be able to read the information that is stored in memory, even if he gains access to the hard drive. Encryption is an extra step to protect your data along with other security measures.
1 Encrypt data on your hard drive. If the data on the hard drive is encrypted, then the hacker will not be able to read the information that is stored in memory, even if he gains access to the hard drive. Encryption is an extra step to protect your data along with other security measures. - Mac - On Mac computers, the FileVault service is used for encryption. To activate, you need to go to the Apple menu in the upper left corner of your device screen, then select System settings, click Protection and securitythen the tab FileVault and finally Enable FileVault... First, you may need to click on the lock icon and enter the password for the administrator account of your current Mac device.
- Windows - BitLocker is the default encryption service on Windows. To activate, simply enter "bitlocker" in the search bar next to the "Start" menu, then click "Bitlocker Drive Encryption" and Turn on BitLocker... Keep in mind that Windows 10 Home users cannot access BitLocker without upgrading to Windows 10 Pro.
 2 Install updates as they are released. In addition to the usual performance improvements, system updates often include security improvements.
2 Install updates as they are released. In addition to the usual performance improvements, system updates often include security improvements.  3 Back up your data regularly. Even the most stringent security measures are not a guarantee of absolute protection. Hacking and even a simple computer malfunction can become a problem. Thanks to backups, you will not lose your data.
3 Back up your data regularly. Even the most stringent security measures are not a guarantee of absolute protection. Hacking and even a simple computer malfunction can become a problem. Thanks to backups, you will not lose your data. - There are cloud services that can be used for backups. Before using it, you should make sure that the service is safe. Resist the temptation to use the cheapest option if you want to protect your data.
- You can also use an encrypted external hard drive for backups. Set up your computer to automatically back up your data every day at times when you do not normally use your machine.
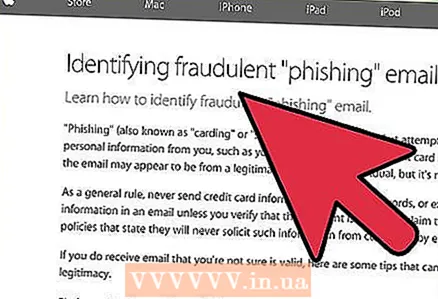 4 Don't click on suspicious links or reply to unknown emails. If you receive an unexpected letter, the sender of which cannot be identified, then you should treat it as a hacking attempt. Do not follow the links in this letter and do not provide the sender with your personal information.
4 Don't click on suspicious links or reply to unknown emails. If you receive an unexpected letter, the sender of which cannot be identified, then you should treat it as a hacking attempt. Do not follow the links in this letter and do not provide the sender with your personal information. - Keep in mind that even a reply to an email will show the sender that your email address is correct and valid. Resist the temptation to write a sarcastic response, because even a response letter may contain information the attacker needs.
 5 Install or activate a firewall. Windows and Mac computers have a firewall that prevents attackers from gaining access to your device. However, on some computers, the firewall may not be enabled by default.
5 Install or activate a firewall. Windows and Mac computers have a firewall that prevents attackers from gaining access to your device. However, on some computers, the firewall may not be enabled by default. - Open your computer's security settings and find the "firewall" item. Enable this function to block incoming connections.
- When using a wireless network, this function is usually available on the router.
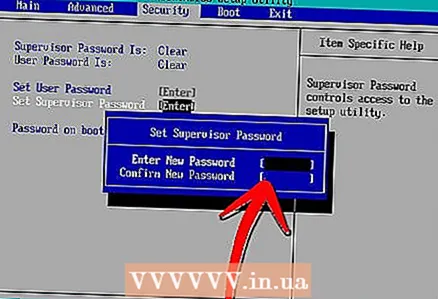 6 Enable passwords for firmware. If this feature is available on your computer, enable password entry to reboot from disk or enable single user mode. An attacker would not be able to bypass such a password without physical access to the machine, but be especially careful not to lose or forget such a password, as reset is incredibly difficult. How to set the firmware password:
6 Enable passwords for firmware. If this feature is available on your computer, enable password entry to reboot from disk or enable single user mode. An attacker would not be able to bypass such a password without physical access to the machine, but be especially careful not to lose or forget such a password, as reset is incredibly difficult. How to set the firmware password: - Mac - restart your device then hold ⌘ Command and R while loading. Click Utilities, then Firmware password utility, Enable firmware password and create a password.
- Windows - restart your computer, then hold down the BIOS entry key (usually this Esc, F1, F2, F8, F10, Del) while loading. Use the arrows on the keyboard to select the password setting item, then enter the desired password.
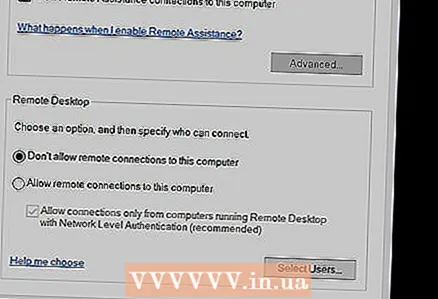 7 Disable remote access. Sometimes you need to get remote access to the computer yourself or open access for technical support. By default, it is better to disable this function and enable it only as needed for a short time.
7 Disable remote access. Sometimes you need to get remote access to the computer yourself or open access for technical support. By default, it is better to disable this function and enable it only as needed for a short time. - The included remote access will effectively become an open door for intruders who wish to break into your computer and steal data.
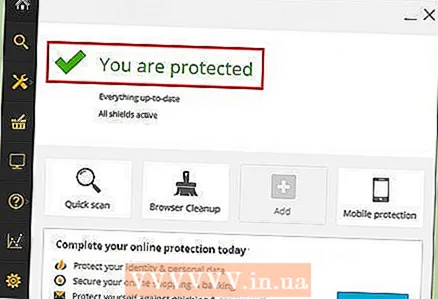 8 Install an antivirus. Antivirus programs recognize and remove potentially dangerous files and programs as soon as they are downloaded. For PCs, Windows Defender is a good choice, which comes preinstalled on the Windows 10 operating system. For Mac computers, you should use AVG or McAfee as another line of defense in addition to the Gatekeeper service, which is designed to protect the system by default.
8 Install an antivirus. Antivirus programs recognize and remove potentially dangerous files and programs as soon as they are downloaded. For PCs, Windows Defender is a good choice, which comes preinstalled on the Windows 10 operating system. For Mac computers, you should use AVG or McAfee as another line of defense in addition to the Gatekeeper service, which is designed to protect the system by default. - It also doesn't hurt to make sure that your firewall and Bluetooth service only allow access to your computer over secure connections.
Method 4 of 4: How to Ensure Network Security
 1 Use secure wireless networks. In general, secure networks require you to enter a password before connecting. In some places (like airports and cafes), you can ask for a password after making a purchase.
1 Use secure wireless networks. In general, secure networks require you to enter a password before connecting. In some places (like airports and cafes), you can ask for a password after making a purchase. - If the wireless network is not secured, the computer will inform you before connecting.Also, on some operating systems, an exclamation mark will be displayed next to the network name.
- If you need to access the Internet, but there is no secure network nearby, then change all passwords immediately after the next connection to a secure network.
- Use a secure and encrypted wireless network at home. It is important to remember that wireless routers are usually not secured by default, so you need to ensure security yourself.

Chiara corsaro
Phone and Computer Repair Technician Chiara Corsaro is the General Manager and Apple Certified Mac and iOS Technician at macVolks, Inc., an Apple Authorized Service Center in the San Francisco Bay Area. MacVolks, Inc. founded in 1990, accredited by the Bureau of Better Business (BBB) with an A + rating and is part of the Apple Consultants Network (ACN). Chiara corsaro
Chiara corsaro
Telephone and computer repair technicianOur expert confirms: To protect your computer from hackers, always connect to the Internet only through a secure network. It is better not to use public networks, because they are the main security threat to your computer outside the home.
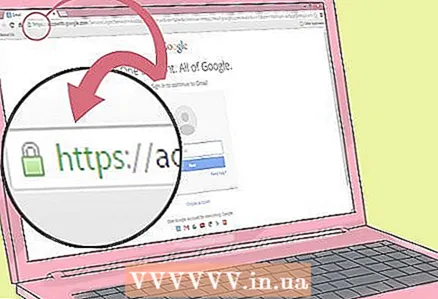
 2 Download programs only on reliable sites. Do not use programs from sites that you visit with an unsecured connection. If there is no padlock icon in the address bar and no “HTTPS” symbols in front of “www”, it is best not to visit this site at all (and not to download files).
2 Download programs only on reliable sites. Do not use programs from sites that you visit with an unsecured connection. If there is no padlock icon in the address bar and no “HTTPS” symbols in front of “www”, it is best not to visit this site at all (and not to download files).  3 Learn to recognize fake sites. In addition to the "HTTPS" symbols and the lock icon to the left of the address, double-check the text of the site address before entering the password on the page. Some sites will try to steal your login information and impersonate other well-known sites - these are called phishing sites. Usually, in this case, some letters, symbols and hyphens are present or absent in the address line.
3 Learn to recognize fake sites. In addition to the "HTTPS" symbols and the lock icon to the left of the address, double-check the text of the site address before entering the password on the page. Some sites will try to steal your login information and impersonate other well-known sites - these are called phishing sites. Usually, in this case, some letters, symbols and hyphens are present or absent in the address line. - For example, a site with the address faceboook.com can impersonate Facebook.
- Sites in which several words are separated by dashes (words between "www" and ".com") should also generally be considered untrustworthy.
 4 Don't use file sharing services. These sites not only violate intellectual property laws, but are also teeming with hackers. You may think that you are downloading a new movie or a fresh hit, but the file may be a virus or malware in disguise.
4 Don't use file sharing services. These sites not only violate intellectual property laws, but are also teeming with hackers. You may think that you are downloading a new movie or a fresh hit, but the file may be a virus or malware in disguise. - Many files are designed in such a way that the virus and malware hidden in them cannot be recognized by antivirus scanning. The system will not become infected until you play the file.
 5 Shop only from trusted stores. Do not enter your bank card details on sites without the "https: //" symbols in front of the "www" part in the page address. The letter "s" indicates that the site is protected. Other sites do not encrypt or protect your data.
5 Shop only from trusted stores. Do not enter your bank card details on sites without the "https: //" symbols in front of the "www" part in the page address. The letter "s" indicates that the site is protected. Other sites do not encrypt or protect your data.  6 Do not share personal information on social media. You may feel like you are only sharing data with your friends, but disclosing personal information about yourself and your life on a social network can leave you vulnerable to hacks. Share information directly with people, not in open publications.
6 Do not share personal information on social media. You may feel like you are only sharing data with your friends, but disclosing personal information about yourself and your life on a social network can leave you vulnerable to hacks. Share information directly with people, not in open publications.
Tips
- You can find free and paid versions of firewalls and antiviruses on the Internet.
- Your password must not be the same username or email address.
Warnings
- Alas, but the only one hundred percent protection against hacking will only be a complete rejection of technology.
- The presence of the green padlock and the HTTPS element does not mean that the site is official yet. It is required to double-check the address and always type it yourself, and not follow the link in the letter.