Author:
Carl Weaver
Date Of Creation:
22 February 2021
Update Date:
1 July 2024

Content
There is no reliable way to tell if a computer has been compromised, unless the computer is not connected to the Internet. But there are several ways to reduce the likelihood of being hacked.
Steps
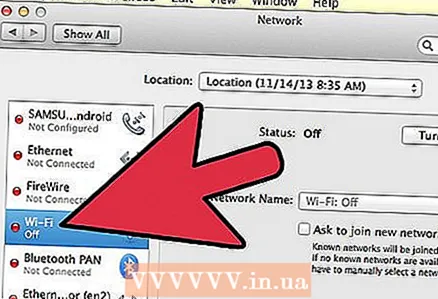 1 Disconnect your computer from the internet.
1 Disconnect your computer from the internet. 2 Open Control Panel and click on "Uninstall Programs". Now remove unnecessary or all antivirus programs (leave the antivirus only if it works for you). Remember that several antiviruses will conflict with each other, further compromising the security of your computer.
2 Open Control Panel and click on "Uninstall Programs". Now remove unnecessary or all antivirus programs (leave the antivirus only if it works for you). Remember that several antiviruses will conflict with each other, further compromising the security of your computer.  3 Protect your computer. If your computer has all the software you need to protect against viruses, malware, and hacker attacks, skip to step eight. Otherwise, install the following (or missing) programs:
3 Protect your computer. If your computer has all the software you need to protect against viruses, malware, and hacker attacks, skip to step eight. Otherwise, install the following (or missing) programs: - Antivirus with real-time heuristic scanning such as Comodo BoClean or AVG Free.
- Anti-spyware such as HijackThis or Spybot S&D.
 4 Install a firewall (to replace the weak built-in Windows firewall), for example ZoneAlarm.
4 Install a firewall (to replace the weak built-in Windows firewall), for example ZoneAlarm. 5 Use intrusion detection software.
5 Use intrusion detection software. 6 Install the required programs. Then connect your computer to the Internet and update the databases of these programs.
6 Install the required programs. Then connect your computer to the Internet and update the databases of these programs.  7 Run your antivirus and antispyware software. If someone has compromised your computer, the malware will be detected and most likely removed.
7 Run your antivirus and antispyware software. If someone has compromised your computer, the malware will be detected and most likely removed.  8 Keep your operating system, anti-virus software, and anti-spyware up to date. Do this at least once a week. This can prevent almost any attack (provided that you use your computer correctly, for example, do not open suspicious sites).
8 Keep your operating system, anti-virus software, and anti-spyware up to date. Do this at least once a week. This can prevent almost any attack (provided that you use your computer correctly, for example, do not open suspicious sites).
Tips
- If possible, set your browser to block trackers and set it to the highest level of security and privacy.
- Use an alternative browser. For example, Firefox, Google Chrome and Opera are much more secure than Internet Explorer, which has a lot of vulnerabilities. This will increase the security of your computer.
Warnings
- Do not open untrustworthy or suspicious sites. If you see a long list of irrelevant and unrelated words in the search results, this is most likely a malicious site.
- Don't open attachments in emails - first contact the sender and find out what the attachment is. Even if the letter came from a person you know, this does not mean that there are no viruses on his computer. The virus can automatically attach itself to emails and send itself to all contacts without the knowledge of the computer owner.
- Do not install ActiveX controls from untrusted sites.
- Do not run applications or copy files from disks and flash drives that belong to other people (even your friends), or from your drives that you connected to other devices - check the drive with antivirus first. Remember that a virus can penetrate from an infected computer to an external storage medium.
- Read the license agreement before installing the program. Many malicious programs are installed during the installation of the programs you want, and such malicious programs are mentioned in the license agreement. If anything in the text of the agreement confuses you, do not install the program. Pay attention to the additional programs that will be installed along with the main program. Remember that it is easier to refuse installation than to uninstall such "additional" programs.