Author:
Ellen Moore
Date Of Creation:
19 January 2021
Update Date:
2 July 2024
Content
Downloading software has become a stressful task. In a world where anonymity matters a lot, there are people who “neglect privacy” and follow your every move. However, there are many things that can be uploaded and downloaded anonymously. This approach will be explored below.
Steps
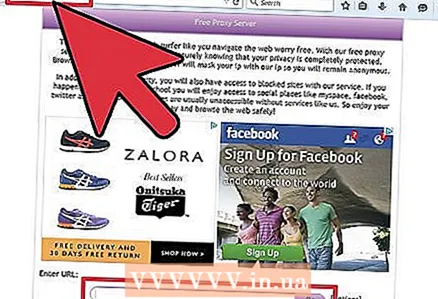 1 There are many ways to hide your tracks on the information highway. The main way people leave a mark on a computer is their IP address. This number can easily be converted into a real address with minimal effort. Therefore, almost all anonymous services are performed exclusively with IP addresses. IP Anti-Discovery can be divided into two categories. Namely:
1 There are many ways to hide your tracks on the information highway. The main way people leave a mark on a computer is their IP address. This number can easily be converted into a real address with minimal effort. Therefore, almost all anonymous services are performed exclusively with IP addresses. IP Anti-Discovery can be divided into two categories. Namely: - software based:
- Proxy: A proxy, in simple terms, is another proxy computer that reflects a connection to a required resource. You can download add-ons for Firefox so that these proxy "addresses" can be entered.
- List Blocking: A blocking list is made up of various addresses of computers that people want to block from connecting to themselves. With this service it is possible to block government sites, RIAA, Spyware sites and even ads to some extent. A popular free block list tool is called Peer Guardian.
- Bounce Link: Some hosting sites allow you to download a link that they themselves have thanks to user uploads.After specifying the "disclaimer", they really do not take any responsibility for the links that users download, some even delete the IP address logs; or
- hardware-based: by adding or removing certain parts to / from a computer, a person can achieve a level of high anonymity.
- NIC-USB: By removing the internet card, you will achieve perfect anonymity. Can't they go right through the power cord? However, if you want to stay connected, it might be better to invest in equipment. Get yourself a large data recovery disc, that is, a huge USB flash drive. Install the operating system and all you need to do (to use the random BIOS setting of computers) is to boot the computer from USB. This is very convenient to use in pizzerias with high Internet speed, or even in some cafes. However, you will have to remain anonymous in real life and will eventually have to learn the most modern SSH protocols.
- Differential Porting: Two computers can be linked together using parallel or serial cables as well, given the appropriate hardware and software circumstances. Using this method, multiple computers can be linked together with mixed proxies and ports to confuse anyone using Peeper.
- Airsnorting: With a wireless laptop, you can sit outside the cafe. Using an unnamed Linux application, you can find invisible encryption keys that "flow through the air" during wireless transmission, thus providing you with a "golden key" to connect them. This, combined with the SSH protocol, will take you online almost anywhere.
- SSH protocol: With a small PirateRay app that uses an SSH secure tunnel on one of the PirateRay servers, the user can either select a specific server or set options to allow random server selection whenever the app starts =.
- software based:
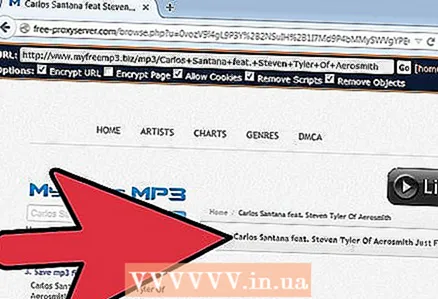 2 After that, all data that the user receives or transmits is encrypted.
2 After that, all data that the user receives or transmits is encrypted.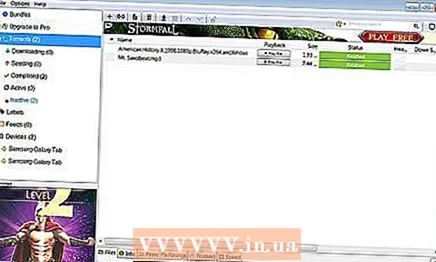 3 All operations related to the torrent network will be performed from the IP address of a server located on the other side of the world. Login is not performed on the same servers, so the user can be sure of their security and anonymity.
3 All operations related to the torrent network will be performed from the IP address of a server located on the other side of the world. Login is not performed on the same servers, so the user can be sure of their security and anonymity.
Warnings
- The best way to avoid getting caught is by not doing anything illegal. Look for legal alternatives whenever possible, even if it's not so convenient.
- Anyone who is as strong as the RIAA can break anonymity given enough time. This is true no matter how hard you try; your traffic still has to go through many routers and servers.
- The only truly anonymous connection is to put it in your pocket and take it with you.
- IP addresses are never invisible. Using a proxy can slow down the detection, but the download process will never go "without a trace". Also note that proxies slow down your internet speed significantly.
- Laptops have IP addresses, just like desktop computers.



