Author:
Eric Farmer
Date Of Creation:
9 March 2021
Update Date:
1 July 2024

Content
- Steps
- Method 1 of 3: Computer spying
- Method 2 of 3: Corporate Espionage
- Method 3 of 3: Espionage in your personal life
- Tips
Spies don't just exist in James Bond films. Computer and corporate espionage are two common ways of spying on people and stealing data in the modern world. There is also always the danger of being stalked and spied on, especially thanks to the technology available to the determined and determined spy. If you have reason to believe that you or your company is being tracked, there are a number of ways to identify spies. Be fully armed to avoid falling prey to intruders.
Steps
Method 1 of 3: Computer spying
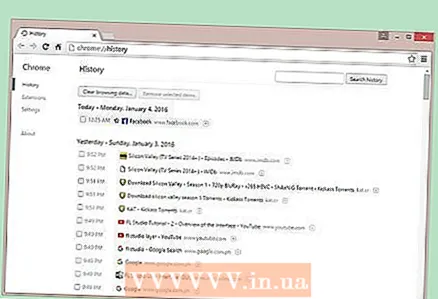 1 Check your browser history. If the list contains suspicious sites or pages that you have not visited, then there is a possibility that your computer is being used by others. Also, if the search history has been cleared, and you have not done so, then someone else may be involved. In this case, you are being monitored through direct access to your PC.
1 Check your browser history. If the list contains suspicious sites or pages that you have not visited, then there is a possibility that your computer is being used by others. Also, if the search history has been cleared, and you have not done so, then someone else may be involved. In this case, you are being monitored through direct access to your PC. - Remember to turn off your computer after use, or set a strong password that includes letters, numbers, and symbols to protect your device from unauthorized users.
 2 Check your computer for third-party software. Such programs work over virtual computer networks and allow you to remotely access your computer while it is turned on. Many people use programs like LogMeIn or GoToMyPC to work remotely. If you have such a program installed and a stranger finds out your login information, then he will be able to access your PC from a remote location.
2 Check your computer for third-party software. Such programs work over virtual computer networks and allow you to remotely access your computer while it is turned on. Many people use programs like LogMeIn or GoToMyPC to work remotely. If you have such a program installed and a stranger finds out your login information, then he will be able to access your PC from a remote location. 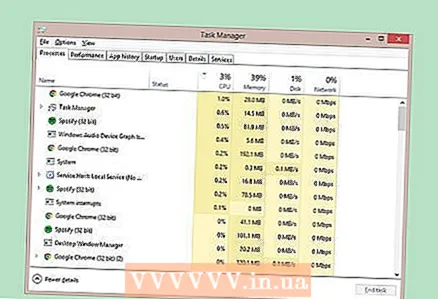 3 Monitor the speed of your computer and other devices. If the speed starts to decrease, then a similar situation may be caused by surveillance of you via the Internet.The tracking software uses a lot of memory and slows down your computer. View applications running on your PC for unfamiliar programs.
3 Monitor the speed of your computer and other devices. If the speed starts to decrease, then a similar situation may be caused by surveillance of you via the Internet.The tracking software uses a lot of memory and slows down your computer. View applications running on your PC for unfamiliar programs. - Popular commercial antivirus programs like Symantec, McAfee, and Norton can detect malicious software.
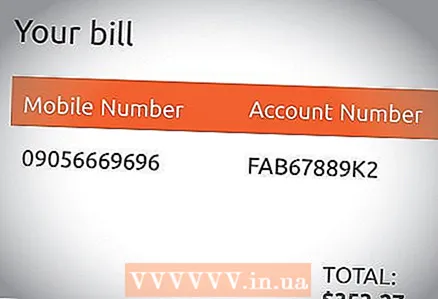 4 Check invoices. If a third party has access to your devices, they may also have access to your personal information, which can be used to steal your identity. In addition, spyware on the phone uses the GPS navigation system to send tracking data, which can increase mobile bills.
4 Check invoices. If a third party has access to your devices, they may also have access to your personal information, which can be used to steal your identity. In addition, spyware on the phone uses the GPS navigation system to send tracking data, which can increase mobile bills. 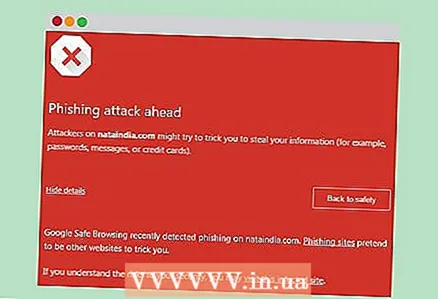 5 Downloads from untrustworthy sites. When downloading data from pages on the Internet, always use your computer security system to check the reliability of the site. When downloading files from sites marked as unsafe, there is a risk of providing access to your computer to third parties.
5 Downloads from untrustworthy sites. When downloading data from pages on the Internet, always use your computer security system to check the reliability of the site. When downloading files from sites marked as unsafe, there is a risk of providing access to your computer to third parties.
Method 2 of 3: Corporate Espionage
 1 Important company information and data access. Think about what type of information your competitors might be interested in. This could be important research, corporate strategy, or even accounting summaries. If unauthorized persons gain access to such information, then the situation may include all signs of corporate espionage.
1 Important company information and data access. Think about what type of information your competitors might be interested in. This could be important research, corporate strategy, or even accounting summaries. If unauthorized persons gain access to such information, then the situation may include all signs of corporate espionage.  2 Legal and illegal activities. Most often, corporate espionage involves the search and analysis of publicly available information. Such data may include a list of employees, plans for future events or sales, recent changes in the structure of the company. A person who obtains information through legal methods can pose a threat to the company and still not commit criminal activity. Only fraud, burglary and penetration, theft and other illegal activities are the reason for accusations of corporate espionage and subsequent legal proceedings.
2 Legal and illegal activities. Most often, corporate espionage involves the search and analysis of publicly available information. Such data may include a list of employees, plans for future events or sales, recent changes in the structure of the company. A person who obtains information through legal methods can pose a threat to the company and still not commit criminal activity. Only fraud, burglary and penetration, theft and other illegal activities are the reason for accusations of corporate espionage and subsequent legal proceedings. - Some employees may inadvertently post information on their personal pages on social networks, reporting the situation in the office, hiring or firing. Such information can be very useful for corporate spies, and the data will be obtained in a completely legal way.
 3 Notice unfamiliar faces. Are there people in the building or office that you don't recognize? In many companies, it is impossible to remember the faces of all employees, so strangers can sneak into the building through the back door or enter with the rest of the organization.
3 Notice unfamiliar faces. Are there people in the building or office that you don't recognize? In many companies, it is impossible to remember the faces of all employees, so strangers can sneak into the building through the back door or enter with the rest of the organization. - This will only help you notice the person who should not be in the room. Your company should have a clear reporting process for security breaches. Please report the situation in accordance with the regulations in force.
 4 Pay attention to unusual activities. Watch your employees' actions for unusual behavior. If someone starts to view more files than usual, or does it from another place (for example, from home), then it is possible that he is collecting data for third parties.
4 Pay attention to unusual activities. Watch your employees' actions for unusual behavior. If someone starts to view more files than usual, or does it from another place (for example, from home), then it is possible that he is collecting data for third parties. - Examining the contents of trash cans is an easy way to gather information about a company. If you notice a person rummaging through your company's trash cans (and this is not an employee trying to find an accidentally discarded document), then he may turn out to be a corporate spy.
 5 Social engineering methods. Often corporate spies just talk to people and ask leading questions. They can call and impersonate employees who have forgotten their username or password. Try to notice strange questions or attempts to intimidate the person to get the information you need.
5 Social engineering methods. Often corporate spies just talk to people and ask leading questions. They can call and impersonate employees who have forgotten their username or password. Try to notice strange questions or attempts to intimidate the person to get the information you need. - Also, so-called "phishing" schemes can be used, when a stranger introduces himself as an employee of the information department or other important employee of the company and tries to find out passwords or various data.
- Train employees to pay attention to certain leading questions or certain social cues that may be hiding spying attempts. Establish a clear order of communication of classified information. If the order is not followed, then this is a direct signal of danger.
Method 3 of 3: Espionage in your personal life
 1 Watch your surroundings. Do not walk down the street with headphones or looking at your phone. It's easier to chase you this way, since you don't follow what's going on around you.
1 Watch your surroundings. Do not walk down the street with headphones or looking at your phone. It's easier to chase you this way, since you don't follow what's going on around you.  2 Watch out for other cars. Pay attention to inconspicuous cars. As a rule, spies do not choose flashy vehicles. Also, start noticing familiar cars that belong to people you know, because they too may have reasons to follow you.
2 Watch out for other cars. Pay attention to inconspicuous cars. As a rule, spies do not choose flashy vehicles. Also, start noticing familiar cars that belong to people you know, because they too may have reasons to follow you. - While driving, try to slow down a little and see if the driver of the car following you does the same. On the highway, try changing lane and see what the other driver does.
- It is unlikely that a spy will follow you in a bright and expensive car. They usually use inconspicuous machines that dissolve in the flow and do not attract attention. If you seem to be being followed, look for distinctive signs such as license plates on your car.
 3 Spot hidden cameras. There are many small cameras that can be easily overlooked. They can be installed in hidden places or embedded in another object to discreetly record your actions. These cameras are diminutive in size, so try to notice such small items that may look out of place, as well as strange wires that at first glance do not lead anywhere.
3 Spot hidden cameras. There are many small cameras that can be easily overlooked. They can be installed in hidden places or embedded in another object to discreetly record your actions. These cameras are diminutive in size, so try to notice such small items that may look out of place, as well as strange wires that at first glance do not lead anywhere. - Use your smartphone to detect cameras. Turn off the lights in the room and turn on the camera on your smartphone. Inspect the room through the lens. Night vision cameras send bright red signals (thanks to which they can see in the dark), which will be visible on the smartphone screen. This will help you find hidden cameras.
- Various devices for finding hidden cameras can be purchased today. A small apparatus produces a high-frequency red light signal, with which you need to explore the room. Such light will reflect off lenses, chips, or infrared light sources.
 4 Find listening devices. If your phone makes strange sounds even after you end a call, you may be overheard. Eavesdropping devices can also interfere with electronic devices such as televisions and radios.
4 Find listening devices. If your phone makes strange sounds even after you end a call, you may be overheard. Eavesdropping devices can also interfere with electronic devices such as televisions and radios. 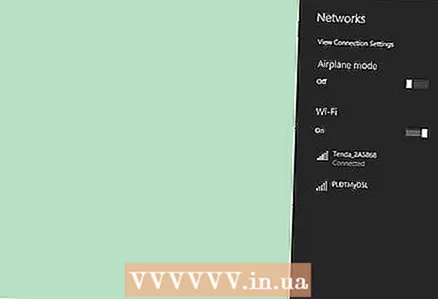 5 Be aware of unusual Wi-Fi networks. Hidden devices like cameras or recording devices can use Wi-Fi networks to transfer data. If your phone or laptop picks up a strong signal in your home that does not belong to your network, then it is possible that this network is being used by outsiders.
5 Be aware of unusual Wi-Fi networks. Hidden devices like cameras or recording devices can use Wi-Fi networks to transfer data. If your phone or laptop picks up a strong signal in your home that does not belong to your network, then it is possible that this network is being used by outsiders.
Tips
- Many companies monitor their employees' computers and network activity, so don't be surprised if you are being monitored during business hours.
- Read books and articles on how to become a spy. They may contain clues that will allow you to spot the spy in real life.
- If you are being harassed or sent letters with threats and blackmail, then you need to urgently contact the law enforcement agencies. The actions of the aggressor may not be related to espionage in any way, but safety comes first.