Content
The Internet is an important part of many people's lives. Some of us use the Internet all day long. However, the constant use of the Internet is associated with the risk of contamination of equipment with viruses and malware. All of this can lead to data loss and identity theft. Every Internet user should know how to prevent infection with a virus, as well as be able to recognize the signs of infection. In this article, you will find information that will allow you to surf the Internet safely.Armed with the knowledge of preventing infection and the spread of viruses, you will make the Internet safer for yourself and for everyone with whom you communicate there.
Steps
Method 1 of 2: Security Features
- 1 Check your computer settings. At a minimum, you must have a firewall installed, and also have a reliable antivirus of the latest version. The computer should automatically install updates for all applications.
- Learn to check and install updates on Windows 10 or Mac OS.
- 2 Install a reliable antivirus. Be aware that you may not need to install additional antivirus programs on new computers, as in many cases they come with built-in antivirus features that work better than third-party applications. But if you decide to install the antivirus yourself, download the application only from a trusted source, as many viruses can make you think that there are malicious files on your computer, even if they are not. The following applications are considered reliable:
- Microsoft Security Essentials (Windows 7 only)
- Norton
- McAfee
- MalwareBytes
- 3 Install a reliable antivirus extension. Due to the architecture of modern browsers, antivirus applications cannot function as extensions themselves - they need to be installed in browsers. It is important to only download extensions from trusted sources, as some viruses can tell you that a site is dangerous even when it is not.
- Windows Defender Browser Protection (Google Chrome only)
- Norton extensions
- McAfee WebAdvisor
- Malwarebytes extensions

Luigi Oppido
Computer Repair Technician Luigi Oppido is the owner and technician of Pleasure Point Computers, a computer repair company in Santa Cruz, California. Has over 25 years of experience in computer repair, update, data recovery and virus removal. He has also been broadcasting the Computer Man Show for over two years! at KSCO in Central California. Luigi Oppido
Luigi Oppido
Computer repair technicianOur expert agrees with this. The best protection at the moment is provided by browser extensions such as AdBlock.
- 4 Make backups and store them in a remote location. It can be a cloud or a remote hard drive on the network. If you store all your files on the Internet, they are less likely to be infected with a virus. Do not make copies to external hard drives, as the virus can damage them.
Method 2 of 2: Good New Habits
 1 Don't click on everything. The internet is full of banners and pop-up ads that are designed to grab the user's attention and force them to click on a link. Due to the way modern browsers work on the Internet, it is quite difficult to catch a virus if you don't click on anything. This means you shouldn't click on banners or offers that seem too good to be true.
1 Don't click on everything. The internet is full of banners and pop-up ads that are designed to grab the user's attention and force them to click on a link. Due to the way modern browsers work on the Internet, it is quite difficult to catch a virus if you don't click on anything. This means you shouldn't click on banners or offers that seem too good to be true. - Make sure your browser is set up so that it will always ask you if you agree to run the file and will not automatically download anything. If you confirm every action, the likelihood of infection will be much lower.
 2 Be aware that some pop-ups may be fake. Some pop-ups mimic reliable antivirus software. These pop-ups try to trick the user into thinking that the antivirus has detected an infected file, but when the user clicks on this window, the infected file starts to install.
2 Be aware that some pop-ups may be fake. Some pop-ups mimic reliable antivirus software. These pop-ups try to trick the user into thinking that the antivirus has detected an infected file, but when the user clicks on this window, the infected file starts to install. - Don't click on the link. Close the pop-up window and open the antivirus on your computer. You will most likely not find any warnings there. If you are still worried about a potential threat, scan your computer with the application installed on it.
- Do not click on the cross to close the pop-up, as more windows will likely open after that. Close the window using the task manager. You can also install an ad blocker to help you avoid annoying ads.
- Some pop-ups may alert you to a threat that only their product can address. None of the trusted antivirus companies will advertise themselves in this way, so do not click on links in such windows.
- Configure your browser so that it doesn't show you pop-ups.
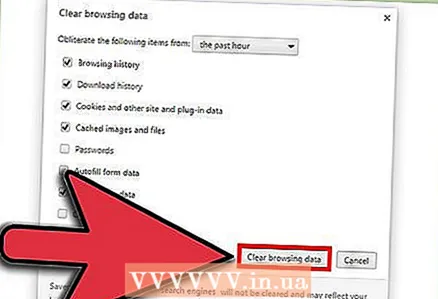 3 Clear your browser cache. Pop-ups can store information in the browser's cache, causing them to pop up constantly again. To prevent this from happening, clear your cache regularly.
3 Clear your browser cache. Pop-ups can store information in the browser's cache, causing them to pop up constantly again. To prevent this from happening, clear your cache regularly.  4 Don't go to sites you shouldn't go to. Since all viruses are illegal, there are a lot of them on illegal sites. Do not go to sites where you can illegally download applications, music or videos, as well as other illegal sites. By downloading files, you can infect your computer with a virus. If you don't do what you can't do, your computer will be less susceptible to attacks.
4 Don't go to sites you shouldn't go to. Since all viruses are illegal, there are a lot of them on illegal sites. Do not go to sites where you can illegally download applications, music or videos, as well as other illegal sites. By downloading files, you can infect your computer with a virus. If you don't do what you can't do, your computer will be less susceptible to attacks. - On such sites, you can not only download the virus along with the file, but also see many pop-ups and fraudulent ads. All this can lead to infection of the computer with a virus or spyware.
- 5 Download applications only from trusted sources. Don't install apps from sites you don't know. Even if you know the site (eg download.com, mediafire.com), be careful.
- On Windows 10, you can activate alerts or even block the download or installation of desktop apps.
- MacOS computers warn the user when installing applications from outside the App Store.
- 6 Don't click on links in emails. By clicking on the link, you can install the malicious application. If necessary, manually copy the address into a string. This will allow you to spot a suspicious address in time.
- Some email services check links. Don't rely on this entirely - use this option as a way to prevent the installation of a malicious application.

Luigi Oppido
Computer Repair Technician Luigi Oppido is the owner and technician of Pleasure Point Computers, a computer repair company in Santa Cruz, California. Has over 25 years of experience in computer repair, update, data recovery and virus removal. He has also been broadcasting the Computer Man Show for over two years! at KSCO in Central California. Luigi Oppido
Luigi Oppido
Computer repair technicianOur expert agrees. Most often, viruses get to the computer through downloading files and through links in letters. Before clicking on the link in the letter, hover over the link with the cursor and see which address will be displayed in the lower left corner of the browser. This will show you where the link goes before you click on it.
- 7 Don't click on pop-up ads. Typically, these advertisements do not meet modern marketing standards.
- When clicking on an ad from the AdChoices category, remember that some advertisers illegally use this logo to display their ad.
- 8 Don't take surveys or install apps to get free products. Block bots that offer such services and report them to site owners. These surveys only collect personal information and install malware on your computer.
- Don't buy followers, take surveys, or download apps to grow your social media profile. Not worth it give out your personal information to a site that you do not know. Let your social media page develop naturally.
- 9 Do not call the numbers listed in fake support messages. Such messages are sent to obtain personal data, control the computer, demand money and install hard-to-remove malicious applications. If you come across such messages, report them to law enforcement agencies.
- Remember that a real company will not contact you or give you their phone number if your computer is infected with a virus.
 10 Be selective in what you download. There are applications for almost any task, but it's important to consider whether you really need to install all of them. Analyze your task.Perhaps you already have a program that can do what you need to do. Downloading the program for each new task will increase the likelihood that you will install something dangerous.
10 Be selective in what you download. There are applications for almost any task, but it's important to consider whether you really need to install all of them. Analyze your task.Perhaps you already have a program that can do what you need to do. Downloading the program for each new task will increase the likelihood that you will install something dangerous. 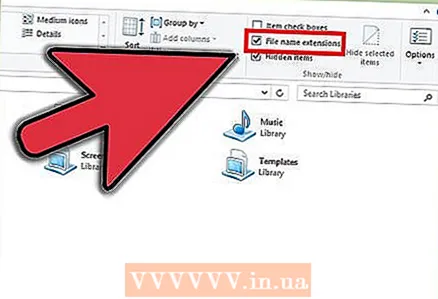 11 Take a look at the extension of the file you want to open. Fraudulent files often have fake extensions that can mislead the user (.txt.vb or .webp.exe). Windows often hides file extensions to make files appear neat in the general list. With double extensions, the second part of the extension is hidden, which poses a danger to the user. If you usually do not see the extension on your computer and suddenly noticed that the file you downloaded has it, it is possible that this is a fake file that is disguised as something else.
11 Take a look at the extension of the file you want to open. Fraudulent files often have fake extensions that can mislead the user (.txt.vb or .webp.exe). Windows often hides file extensions to make files appear neat in the general list. With double extensions, the second part of the extension is hidden, which poses a danger to the user. If you usually do not see the extension on your computer and suddenly noticed that the file you downloaded has it, it is possible that this is a fake file that is disguised as something else. - To make file extensions always visible, open Explorer (Windows Explorer), click on "View" and select "Settings". Click on "View" in the "Folder Options" menu and remove the checkbox from the "Hide extensions for known file types" field.
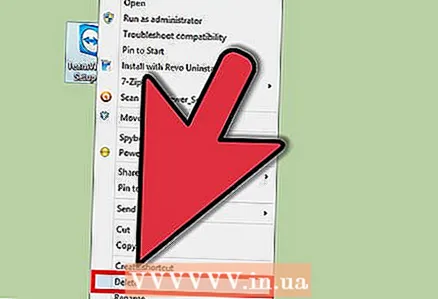
 12 Check downloaded files. If you have antivirus installed, train yourself to scan files that you downloaded from unknown locations. Most antiviruses allow you to instantly check suspicious files. To do this, right-click on the file and select antivirus in the drop-down menu.
12 Check downloaded files. If you have antivirus installed, train yourself to scan files that you downloaded from unknown locations. Most antiviruses allow you to instantly check suspicious files. To do this, right-click on the file and select antivirus in the drop-down menu. - Always check ZIP files with your antivirus, as an archive can contain multiple files.
- Email services often scan files in applications automatically, but you should still check the downloaded files yourself.
- Both Windows and MacOS can scan files for malicious elements.
 13 Don't open files you don't trust. A virus or worm cannot do anything unless you launch the application with which it is associated. This means that downloading the file alone will not do anything to your computer. If after downloading you decide that you do not trust the file, do not open it or delete it. Do not touch the file if you cannot be sure of its reliability.
13 Don't open files you don't trust. A virus or worm cannot do anything unless you launch the application with which it is associated. This means that downloading the file alone will not do anything to your computer. If after downloading you decide that you do not trust the file, do not open it or delete it. Do not touch the file if you cannot be sure of its reliability.  14 Read the license agreements. You have probably seen these long conditions more than once and accepted them without looking before installing the program. Unscrupulous companies take advantage of the fact that most people do not read these terms and conditions and insert clauses about installing malware into the text. Read the license agreements, especially if you don't know anything about the company.
14 Read the license agreements. You have probably seen these long conditions more than once and accepted them without looking before installing the program. Unscrupulous companies take advantage of the fact that most people do not read these terms and conditions and insert clauses about installing malware into the text. Read the license agreements, especially if you don't know anything about the company. - Also read the privacy policy. If the app collects your data, you need to know how it will use it.
 15 Do not download attachments from unknown sources. Most often, viruses and other malicious files get to your computer from email attachments. Don't click on a link or attachment in an email from an unknown person. If you are not sure that the letter is not fake, contact the person and find out if he sent you something before downloading.
15 Do not download attachments from unknown sources. Most often, viruses and other malicious files get to your computer from email attachments. Don't click on a link or attachment in an email from an unknown person. If you are not sure that the letter is not fake, contact the person and find out if he sent you something before downloading.  16 Do not download attachments from a source you know, unless you expect it. It is not uncommon for computers to become infected with a virus that sends letters without the owner's knowledge. This means that you may receive a fake email from someone you know. If an email or attachment looks odd, don't click on it. Find out if the person actually sent you the attachment.
16 Do not download attachments from a source you know, unless you expect it. It is not uncommon for computers to become infected with a virus that sends letters without the owner's knowledge. This means that you may receive a fake email from someone you know. If an email or attachment looks odd, don't click on it. Find out if the person actually sent you the attachment.  17 Disable image preview. Many email applications automatically display thumbnails of images, but images may contain malicious code. Download images from the letter only if you trust the sender.
17 Disable image preview. Many email applications automatically display thumbnails of images, but images may contain malicious code. Download images from the letter only if you trust the sender. - Keep in mind that some email services have changed their image processing algorithms to make downloading them safer. For example, Gmail no longer turns off images by default. Find out the safest way to download images from the service you use.
 18 Be wary of strange emails from companies you do business with. Phishing sites often disguise themselves as real letters from companies and insert links into letters that are very similar to real ones. When a user clicks on such links, the user is taken to a fake site with a similar name (for example, "povver" instead of "power"). These sites collect personally identifiable information that you believe you are giving to a trusted company.
18 Be wary of strange emails from companies you do business with. Phishing sites often disguise themselves as real letters from companies and insert links into letters that are very similar to real ones. When a user clicks on such links, the user is taken to a fake site with a similar name (for example, "povver" instead of "power"). These sites collect personally identifiable information that you believe you are giving to a trusted company. - No legitimate company will ask you for passwords or any other personal information via email.
 19 Use external storage with caution. Computers are often infected with viruses via USB drives without the user knowing anything. You can infect a computer simply by inserting a USB drive into it (if autorun is activated on it, which is what happens most often). A virus can also get onto a hard drive from an infected public computer (or even a friend's computer that is not properly protected from viruses), especially if many unknown people use the computer.
19 Use external storage with caution. Computers are often infected with viruses via USB drives without the user knowing anything. You can infect a computer simply by inserting a USB drive into it (if autorun is activated on it, which is what happens most often). A virus can also get onto a hard drive from an infected public computer (or even a friend's computer that is not properly protected from viruses), especially if many unknown people use the computer. - You can share files in other ways, such as storing files in the cloud or sending them by email. You can also disable the autostart of all external devices so that the computer does not get infected automatically via a USB drive, and you can also check the external drive with an antivirus after connecting to an unfamiliar computer. (If you are an advanced user, check if the autorun.inf file on your hard drive has been modified and if there is a running command that associates it with a virus. See if the real files are hidden and if they have been replaced with shortcuts with the same name. associated with a virus. Before doing this, make sure your computer is showing hidden and system files.)
- To disable autorun, search for autorun settings, or go to Control Panel> Default Programs> Change Autorun Settings. Remove the checkbox from autorun for all devices, then return to the menu that opened after connecting the disk and select the option to do nothing. These steps will help prevent accidental virus infection after connecting an infected disk to your computer and spreading the virus. However, this will not help you protect the drive from infection if you connect it to an unknown computer. Check your disk regularly for viruses. You can also set an icon for the drive in the autorun.inf file. If the icon disappears, it means that the disk is infected.
 20 Use remote access with caution. With an increase in the number of connections in the modern world, remote services are increasingly used. This is very convenient, but with a large number of direct connections to your computer, it runs the risk of becoming infected. Consider whether you really need this remote connection and always keep your antivirus apps up to date.
20 Use remote access with caution. With an increase in the number of connections in the modern world, remote services are increasingly used. This is very convenient, but with a large number of direct connections to your computer, it runs the risk of becoming infected. Consider whether you really need this remote connection and always keep your antivirus apps up to date.
Tips
- Back up your personal files regularly. This will be useful if your computer is infected with a virus that will delete all files or prevent you from using them.
- Remember: if something seems suspicious to you, most likely they are trying to deceive you.
- Delete temporary internet files in your browser every day.
- If you need to solve a simple problem (for example, the computer freezes or a blue screen appears), just turn off the computer and turn it back on after 10 seconds.
- Do not take polls that seem suspicious, and never don't pay for something that looks suspicious.
- Don't give your password anybody.
Warnings
- If you don't have a backup of all your files, you run the risk of losing all your files if you get a virus or spyware infection. Scan your computer for malicious files from time to time.