Author:
Gregory Harris
Date Of Creation:
11 August 2021
Update Date:
1 July 2024

Content
- Steps
- Method 1 of 3: SQL Injection
- Method 2 of 3: Cracking the Root Password
- Method 3 of 3: Database flaws
- Tips
- Warnings
To protect your database from hackers, you need to think like a hacker. If you were a hacker, what information would you be looking for? How would you get it? There are many different types of databases and many ways to hack them. Often, hackers try to crack the root password or use an exploit. If you are familiar with SQL statements and basic database concepts, try cracking one of them.
Steps
Method 1 of 3: SQL Injection
 1 Find out if the database has vulnerabilities. For this method, you need to understand database operators. Launch your browser and open the database login page interface. Then enter ‘(one quote) in the username field. Click Sign In. If you receive the error "SQL Exception: Quoted String Not Completed Incorrectly" or "Invalid Character", the database is vulnerable to SQL injection.
1 Find out if the database has vulnerabilities. For this method, you need to understand database operators. Launch your browser and open the database login page interface. Then enter ‘(one quote) in the username field. Click Sign In. If you receive the error "SQL Exception: Quoted String Not Completed Incorrectly" or "Invalid Character", the database is vulnerable to SQL injection.  2 Find the number of columns. Go back to the database login page (or any other address that ends with "id =" or "catid =") and click on the address bar. Press the space after the address and enter order by 1, then press ↵ Enter... Increase the number to 2 and press ↵ Enter... Keep increasing the order until the error appears. The number you entered before the misspelled number will be the actual number of columns.
2 Find the number of columns. Go back to the database login page (or any other address that ends with "id =" or "catid =") and click on the address bar. Press the space after the address and enter order by 1, then press ↵ Enter... Increase the number to 2 and press ↵ Enter... Keep increasing the order until the error appears. The number you entered before the misspelled number will be the actual number of columns. 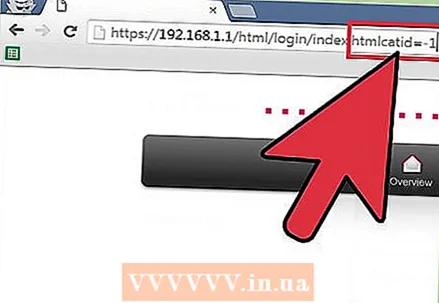 3 Find out which posts are accepting search queries. Find the address bar and change the end of the address from catid = 1 or id = 1 to catid = -1 or id = -1. Press space and type union select 1,2,3,4,5,6 (if there are 6 columns).The count must be up to the total number of columns, with each digit separated by a comma. Click on ↵ Enter and you will see the numbers of all columns that are accepting queries.
3 Find out which posts are accepting search queries. Find the address bar and change the end of the address from catid = 1 or id = 1 to catid = -1 or id = -1. Press space and type union select 1,2,3,4,5,6 (if there are 6 columns).The count must be up to the total number of columns, with each digit separated by a comma. Click on ↵ Enter and you will see the numbers of all columns that are accepting queries. 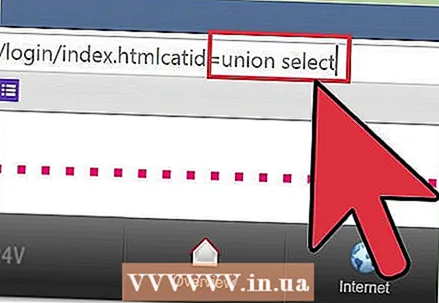 4 Enter SQL statements in the column. For example, if you want to find out the name of the current user and embed the code in column 2, erase everything after id = 1 in the address bar and press the space bar. Then type union select 1, concat (user ()), 3,4,5,6--. Click on ↵ Enter and the screen will display the name of the current database user. Enter various SQL statements to display various information, such as a list of usernames and passwords to crack.
4 Enter SQL statements in the column. For example, if you want to find out the name of the current user and embed the code in column 2, erase everything after id = 1 in the address bar and press the space bar. Then type union select 1, concat (user ()), 3,4,5,6--. Click on ↵ Enter and the screen will display the name of the current database user. Enter various SQL statements to display various information, such as a list of usernames and passwords to crack.
Method 2 of 3: Cracking the Root Password
 1 Try logging in as superuser using the default password. Some databases do not have a default superuser (admin) password, so try logging in with the password blank. Other databases have a default password, which can be easily found on the technical support forum.
1 Try logging in as superuser using the default password. Some databases do not have a default superuser (admin) password, so try logging in with the password blank. Other databases have a default password, which can be easily found on the technical support forum.  2 Try common passwords. If the admin has password-protected the account (which is very likely), try some common username and password combinations. Some hackers publicly post lists of cracked passwords, and they use special cracking programs. Try different combinations of username and password.
2 Try common passwords. If the admin has password-protected the account (which is very likely), try some common username and password combinations. Some hackers publicly post lists of cracked passwords, and they use special cracking programs. Try different combinations of username and password. - You can find your collection of passwords on this trusted site: https://github.com/danielmiessler/SecLists/tree/master/Passwords.
- Entering passwords manually can take a very long time, but try your luck anyway, and only then move on to heavy artillery.
 3 Use a password cracking program. Use various programs and try to crack your password by entering thousands of words and combinations of letters, numbers and symbols.
3 Use a password cracking program. Use various programs and try to crack your password by entering thousands of words and combinations of letters, numbers and symbols. - Popular password cracking programs are: DBPwAudit (for Oracle, MySQL, MS-SQL and DB2) and Access Passview (for MS Access). With their help, you can crack the password of many databases. You can also find a jailbreak program specifically designed for your database on Google. For example, enter oracle db hack program in the search box if you want to hack the Oracle database.
- If you have an account on the server that hosts the database, run a hash-cracking program (such as John the Ripper) and try to crack the password file. The hash file is located in different places in different databases.
- Download programs only from trusted sites. Study the programs carefully before using them.
Method 3 of 3: Database flaws
 1 Find the exploit. Sectools.org has been compiling a list of various defenses (including exploits) for ten years now. Their programs have a good reputation and are used by system administrators to protect their systems around the world. Open their exploit list (or find them on another trusted site) and look for programs or text files that can penetrate the databases.
1 Find the exploit. Sectools.org has been compiling a list of various defenses (including exploits) for ten years now. Their programs have a good reputation and are used by system administrators to protect their systems around the world. Open their exploit list (or find them on another trusted site) and look for programs or text files that can penetrate the databases. - Another site with a list of exploits is www.exploit-db.com. Go to their website and click on the "Search" link, then find the database you want to hack (for example, "oracle"). Enter the captcha in the appropriate field and click on the search button.
- Be sure to research any exploits you intend to test so you know what to do if a problem occurs.
 2 Find the vulnerable network by wardriving. Wardriving is driving (cycling or walking) around an area with network scanning software enabled (like NetStumbler or Kismet) to look for unsecured networks. Technically, wardriving is legal, but illegal activities from the network that you found through wardriving is not.
2 Find the vulnerable network by wardriving. Wardriving is driving (cycling or walking) around an area with network scanning software enabled (like NetStumbler or Kismet) to look for unsecured networks. Technically, wardriving is legal, but illegal activities from the network that you found through wardriving is not.  3 Take advantage of a database hole from a vulnerable network. If you're doing something that you shouldn't, stay out of your web. Connect over a wireless connection to one of the open networks that you found by wardriving and launch the selected exploit.
3 Take advantage of a database hole from a vulnerable network. If you're doing something that you shouldn't, stay out of your web. Connect over a wireless connection to one of the open networks that you found by wardriving and launch the selected exploit.
Tips
- Always keep important data behind a firewall.
- Be sure to password protect your wireless network to prevent wardrivers from using your home network to launch exploits.
- Find other hackers and ask them for some tips.Sometimes the most useful knowledge about the work of hackers cannot be found in the public domain.
Warnings
- Learn about the laws and consequences of hacking in your country.
- Never try to gain illegal access to a device from your network.
- Logging into someone else's database is illegal.