Author:
Judy Howell
Date Of Creation:
26 July 2021
Update Date:
1 July 2024
Content
- To step
- Method 1 of 3: Check if you are being tracked
- Method 2 of 3: Find out if your phone is being tapped
- Method 3 of 3: Check if your email and computer are being monitored
- Tips
Ever felt like you were being watched? If you suspect that you are being shadowed, you will probably be very tense about it. How do you know who to trust? With a little thought, you can probably determine whether the threat is real or not, or whether it exists only in your head.Check out Step 1 below to learn how to find out if someone is following you and how to shake them off, investigate if your phone is being tapped, and how to protect your emails.
To step
Method 1 of 3: Check if you are being tracked
 Ask yourself why someone would want to follow you. Tracking someone takes time and resources, and most local authorities are not going to waste their time tracking ordinary citizens. Private investigators and an angry ex are a completely different matter. Before you get paranoid, ask yourself if there is anything you should be afraid of.
Ask yourself why someone would want to follow you. Tracking someone takes time and resources, and most local authorities are not going to waste their time tracking ordinary citizens. Private investigators and an angry ex are a completely different matter. Before you get paranoid, ask yourself if there is anything you should be afraid of.  Be careful. The main key to discovering if you are being shadowed is to stay alert to your surroundings all the time. Don't sit with your nose in your phone all the time. Keep your eyes open and monitor the world around you. If you don't pay attention, you will never know if you are being followed.
Be careful. The main key to discovering if you are being shadowed is to stay alert to your surroundings all the time. Don't sit with your nose in your phone all the time. Keep your eyes open and monitor the world around you. If you don't pay attention, you will never know if you are being followed.  Don't look over your shoulder all the time. When you start to engage in suspicious behavior, the person shadowing you will notice and distance yourself or stop following you to try again at a later time. If you feel like you are being followed, keep pretending you don't know.
Don't look over your shoulder all the time. When you start to engage in suspicious behavior, the person shadowing you will notice and distance yourself or stop following you to try again at a later time. If you feel like you are being followed, keep pretending you don't know.  Slow down your pace. This applies to both walking and driving. When you walk, slow down and look at shop windows or on your cellphone. Make sure to keep an eye on your surroundings while doing this. If you are driving, switch to the slow track and keep to the speed limit.
Slow down your pace. This applies to both walking and driving. When you walk, slow down and look at shop windows or on your cellphone. Make sure to keep an eye on your surroundings while doing this. If you are driving, switch to the slow track and keep to the speed limit.  Call the police. If you think you are really being tracked and that you are in danger, then you should call the police immediately. Try to stay in crowded, public places while you wait for a response from the police.
Call the police. If you think you are really being tracked and that you are in danger, then you should call the police immediately. Try to stay in crowded, public places while you wait for a response from the police. - Crowds can help you identify the person following you so that you can pass the description on to the police.
- If you call the police and it turns out that an undercover cop is following you, they will likely back off. If it is someone employed by the government, they will likely be stopped by the police. If it is a private investigator, it may be that the receipt will be thrown and you will be informed of what is going on.
 Do not panic. If you suspect you're being tracked, the dumbest thing to do is to run or drive wildly. Not only will those shadowing you be alerted, but you also risk being involved in an accident.
Do not panic. If you suspect you're being tracked, the dumbest thing to do is to run or drive wildly. Not only will those shadowing you be alerted, but you also risk being involved in an accident.  Change your regular patterns. Make a turn and immediately get back onto the highway. If you are walking, walk around the block again. Usually this will upset the person following you, or make them aware that you know you are being followed.
Change your regular patterns. Make a turn and immediately get back onto the highway. If you are walking, walk around the block again. Usually this will upset the person following you, or make them aware that you know you are being followed.  Don't follow the follower yourself. Some people suggest shadowing the person who is shadowing you to get a better idea of who you are dealing with, but this is usually not a good idea and can be very dangerous.
Don't follow the follower yourself. Some people suggest shadowing the person who is shadowing you to get a better idea of who you are dealing with, but this is usually not a good idea and can be very dangerous.
Method 2 of 3: Find out if your phone is being tapped
 Understand how spyware works. Spy software is installed on a smartphone without the user knowing. Then it can send GPS location, phone calls, text messages and more information. It's incredibly unlikely that your phone has such software installed by a malicious party, but the following steps will make sure you know for sure.
Understand how spyware works. Spy software is installed on a smartphone without the user knowing. Then it can send GPS location, phone calls, text messages and more information. It's incredibly unlikely that your phone has such software installed by a malicious party, but the following steps will make sure you know for sure.  Check the behavior of your phone. Is your phone acting weird? Does it light up when you are not using it, does it just shut off or make squeaking noises? All phones will behave strangely from time to time, but if there is a pattern in them, it could be that spyware is installed on your phone.
Check the behavior of your phone. Is your phone acting weird? Does it light up when you are not using it, does it just shut off or make squeaking noises? All phones will behave strangely from time to time, but if there is a pattern in them, it could be that spyware is installed on your phone.  Keep an eye on your battery. A lot of spyware will put an extra strain on your battery. This can be tricky to notice, especially since your phone's battery will naturally become less efficient over time. Note if there are any dramatic changes in your battery life, as this is a better indication of the presence of programs that are draining it.
Keep an eye on your battery. A lot of spyware will put an extra strain on your battery. This can be tricky to notice, especially since your phone's battery will naturally become less efficient over time. Note if there are any dramatic changes in your battery life, as this is a better indication of the presence of programs that are draining it.  Pay attention to background noise while calling. Often, background noise will naturally occur as a byproduct of a bad connection, but if you hear constant static, clicks and beeps during calls, this could be a possible indication that recording software is running on your phone. This is because some software for making a recording while on a call behaves like a group call.
Pay attention to background noise while calling. Often, background noise will naturally occur as a byproduct of a bad connection, but if you hear constant static, clicks and beeps during calls, this could be a possible indication that recording software is running on your phone. This is because some software for making a recording while on a call behaves like a group call.  Watch for strange text messages. Much spyware is controlled by encrypted text messages. If the program does not function properly, you may receive such messages in your inbox. If you receive messages with random combinations of letters and numbers, your phone may be infected with spyware.
Watch for strange text messages. Much spyware is controlled by encrypted text messages. If the program does not function properly, you may receive such messages in your inbox. If you receive messages with random combinations of letters and numbers, your phone may be infected with spyware.  Check your data usage. Many spy programs, especially the cheaper ones, will use your connection to send collected data. Use a data management app to keep track of which apps use data traffic and how much. If data is sent that you are not aware of, it could be that spy software has been installed.
Check your data usage. Many spy programs, especially the cheaper ones, will use your connection to send collected data. Use a data management app to keep track of which apps use data traffic and how much. If data is sent that you are not aware of, it could be that spy software has been installed.  Check for a jailbreak. If you have an iPhone, the only way to install spy software on it is to jailbreak the phone. Look for Installer, Cydia, or Icy apps in one of your home screens. If you see any of these apps, or apps installed from a source other than the Apple Store, then your phone has been hacked and may have spyware installed on it.
Check for a jailbreak. If you have an iPhone, the only way to install spy software on it is to jailbreak the phone. Look for Installer, Cydia, or Icy apps in one of your home screens. If you see any of these apps, or apps installed from a source other than the Apple Store, then your phone has been hacked and may have spyware installed on it. - You can easily fix an iPhone jailbreak. This will remove all apps that depend on jailbreaking, which means that all spyware will be disabled. Check wikiHow for detailed instructions on how to restore your iPhone.
 Use deception. If you feel like your conversations are being overheard by someone you know, you can catch them by deliberately spreading false information. Call a friend you trust and tell them something that is credible but incorrect, whether about your schedule, your life, or something else. If at some point you find out that people you know have this information, then you know that someone has been listening.
Use deception. If you feel like your conversations are being overheard by someone you know, you can catch them by deliberately spreading false information. Call a friend you trust and tell them something that is credible but incorrect, whether about your schedule, your life, or something else. If at some point you find out that people you know have this information, then you know that someone has been listening.
Method 3 of 3: Check if your email and computer are being monitored
 Rest assured that all workplace computers are monitored. Most large companies have workplace clauses that allow them to monitor what websites you visit, what emails you send, and what programs you run. Please check with your IT department to view this agreement, but just assume that nothing you do at work is private.
Rest assured that all workplace computers are monitored. Most large companies have workplace clauses that allow them to monitor what websites you visit, what emails you send, and what programs you run. Please check with your IT department to view this agreement, but just assume that nothing you do at work is private. 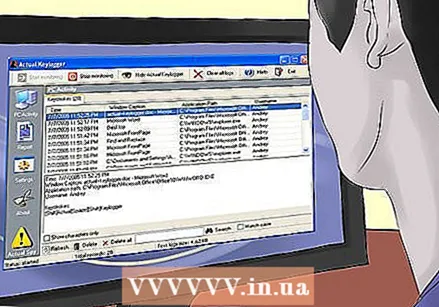 Check for keyloggers. Keyloggers are programs that keep track of every keystroke you make on your computer. They can be used for reconstructing emails and stealing passwords. Keyloggers run in the background and do not show system tray icons or other clear indications that something is going on.
Check for keyloggers. Keyloggers are programs that keep track of every keystroke you make on your computer. They can be used for reconstructing emails and stealing passwords. Keyloggers run in the background and do not show system tray icons or other clear indications that something is going on. - If you are using Windows, press Ctrl+⇧ Shift+Esc to open Task Manager. View the Processes or Background Processes section and keep an eye out for unknown processes. Google anything unknown to see if any keyloggers are active.
- If you are using a Mac, open the Activity Monitor. You can find this program in the Tools folder in the Applications folder. View all active processes and write down anything that is unknown to you. Use Google to find out if they are malicious or not.
- Keyloggers' processes often consume a lot of system resources as they have to keep a fair amount of information.
 Install your own email tracking software. Programs like ReadNotify place small, invisible images in your email so you can track when the email was opened, how long it was opened, and whether it was forwarded. This can be very useful if you are convinced someone is intercepting your messages, as you can track down the IP addresses that opened the email.
Install your own email tracking software. Programs like ReadNotify place small, invisible images in your email so you can track when the email was opened, how long it was opened, and whether it was forwarded. This can be very useful if you are convinced someone is intercepting your messages, as you can track down the IP addresses that opened the email.  Use encryption for your email. If you are really concerned about the possibility that an unauthorized person can read your email, you can switch to an email program that can encrypt your messages. Your email will be encrypted and only recipients you designate can decrypt it. This can be a bit of a hassle to set up, but is essential if you're trying to protect highly sensitive information. See wikiHow for instructions on how to set up encrypted email.
Use encryption for your email. If you are really concerned about the possibility that an unauthorized person can read your email, you can switch to an email program that can encrypt your messages. Your email will be encrypted and only recipients you designate can decrypt it. This can be a bit of a hassle to set up, but is essential if you're trying to protect highly sensitive information. See wikiHow for instructions on how to set up encrypted email.
Tips
- The chances of you being under professional surveillance are extremely slim, so try to avoid becoming overly paranoid.