Author:
Tamara Smith
Date Of Creation:
21 January 2021
Update Date:
1 July 2024

Content
- To step
- Method 1 of 3: Log in without a password
- Method 2 of 3: Get remote access
- Method 3 of 3: Crack a WiFi password (WEP)
- Warnings
Hacking a computer is a useful and sometimes essential skill to master. Below you will find instructions for logging in without a password (useful if you do not remember your password or if you want to check the computer of your child / spouse), to obtain remote access to a computer (to check a user or locate a stolen device) or to crack a Wi-Fi password (useful if you are in an emergency, or if you are lost in an unfamiliar city).
To step
Method 1 of 3: Log in without a password
 Boot the computer in "Safe Mode".
Boot the computer in "Safe Mode". Click on "Start".
Click on "Start". Click on "Run".
Click on "Run". Type: "control userpasswords2".
Type: "control userpasswords2".  Change passwords for one of the user accounts. Of course, the user will soon find out, so you may have to tell a lie.
Change passwords for one of the user accounts. Of course, the user will soon find out, so you may have to tell a lie.  Restart the computer.
Restart the computer.
Method 2 of 3: Get remote access
 Download the "LogMeIn" program. There is a free version, but you can also opt for a subscription.
Download the "LogMeIn" program. There is a free version, but you can also opt for a subscription. - The program must be downloaded to the computer that you want to view or use remotely. It is a useful tool if your computer is stolen or if you have a teenage son or daughter and you want to monitor computer activities.
- You must create an account on the LogMeIn website to use the software.
 Sign up on the LogMeIn website.
Sign up on the LogMeIn website. Go to the "My Computers" page. This page should open automatically when you log in.
Go to the "My Computers" page. This page should open automatically when you log in.  Add the computer you want to access remotely. At the bottom of the page you will see a button that says "Add computer". Click on the button and fill in the required information.
Add the computer you want to access remotely. At the bottom of the page you will see a button that says "Add computer". Click on the button and fill in the required information.  Click on the name of the computer after adding the computer.
Click on the name of the computer after adding the computer. Log in to the computer. This means that you need to know the username and password of the account you want to view.
Log in to the computer. This means that you need to know the username and password of the account you want to view.  Click on "Remote Control". If you are spying on someone, try to move your mouse as little as possible and do not click on anything.
Click on "Remote Control". If you are spying on someone, try to move your mouse as little as possible and do not click on anything.  Sign out when you are done.
Sign out when you are done.
Method 3 of 3: Crack a WiFi password (WEP)
 Download the necessary programs. You need two programs to do this: "CommView" (which looks for weak spots in the network that you want to access) and AirCrackNG (the program with which you crack the password).
Download the necessary programs. You need two programs to do this: "CommView" (which looks for weak spots in the network that you want to access) and AirCrackNG (the program with which you crack the password). - Make sure your computer's wireless network adapter supports CommView.
 Find a network. Use CommView to search for wireless networks. Choose a network with WEP encryption and a fairly strong signal.
Find a network. Use CommView to search for wireless networks. Choose a network with WEP encryption and a fairly strong signal. 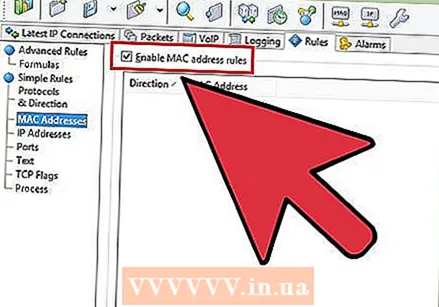 Use the details of the network. Right click on the network, select "Copy MAC address", go to the "Rules" tab and then to "MAC Addresses". Check the box next to "enable MAC address rules" and click Action → Capture → Add Record → Both. Paste the MAC address.
Use the details of the network. Right click on the network, select "Copy MAC address", go to the "Rules" tab and then to "MAC Addresses". Check the box next to "enable MAC address rules" and click Action → Capture → Add Record → Both. Paste the MAC address.  View the "Data Packets". Sort the list so that you only see the Data Packets (D), and not the Management (M) and Control (C) Packets.
View the "Data Packets". Sort the list so that you only see the Data Packets (D), and not the Management (M) and Control (C) Packets.  Save the packets. Go to the "Logging" tab and check the box next to "enable auto saving". You may have to adjust the settings for the size of the folders (Directory) and files (File). Set them to 2000 and 20 respectively.
Save the packets. Go to the "Logging" tab and check the box next to "enable auto saving". You may have to adjust the settings for the size of the folders (Directory) and files (File). Set them to 2000 and 20 respectively.  Click on "Play" to start collecting. Wait until you have collected at least 100,000 packets.
Click on "Play" to start collecting. Wait until you have collected at least 100,000 packets.  Click on "Concatenate Logs" under the "Log" tab. Make sure all logs are selected.
Click on "Concatenate Logs" under the "Log" tab. Make sure all logs are selected.  Export the log files. Go to the folder where the log files are kept and open the log file. Click File → Export → WireShark / tcpdump format and save it where you can easily find it.
Export the log files. Go to the folder where the log files are kept and open the log file. Click File → Export → WireShark / tcpdump format and save it where you can easily find it.  Open your newly created file with Aircrack. Start Aircrack and click on "WEP". Open the file and click "Launch".
Open your newly created file with Aircrack. Start Aircrack and click on "WEP". Open the file and click "Launch".  Enter the index number. When the command prompt window opens, enter the index number for the target network. Probably it is 1. Press Enter and wait. If it works you will now see the password.
Enter the index number. When the command prompt window opens, enter the index number for the target network. Probably it is 1. Press Enter and wait. If it works you will now see the password.
Warnings
- Hacking a computer can have serious consequences, especially when it comes to a public computer or school computer.
- The victim can easily find out that someone has snooped on their computer. So be careful, you can easily get caught.
- Only use these techniques if you have permission from the computer user.