Content
- Steps
- Method 1 of 3: Cheats
- Standard codes
- Code book
- Police coding
- Method 2 of 3: Ciphers
- Date based encryption
- Encryption with a number
- Graphic cipher
- Caesar's rearrangement
- Method 3 of 3: Secret Languages
- Confused language
- Beep code
- Gibberish
- Tips
- Warnings
- What do you need
Give a welcome pai anai iptography Whether you're writing notes to your friends in class or trying to comprehend cryptography (the science of codes and ciphers) for fun, this article can help you learn some basic principles and create your own way to encode private messages. Read step 1 below to find out where to start!
Some people use the words "code" and "cipher" to mean the same concepts, but those who seriously deal with this issue know that they are two completely different concepts. Secret code is a system in which each word or phrase in your message is replaced by another word, phrase or series of characters. A cipher is a system in which each letter of your message is replaced by a different letter or symbol.
Steps
Method 1 of 3: Cheats
Standard codes
 1 Create your own code book. Any complete code requires a code book. Come up with words or phrases to replace the words or phrases you want, then put them all together in a codebook for you to share with your super secret friends.
1 Create your own code book. Any complete code requires a code book. Come up with words or phrases to replace the words or phrases you want, then put them all together in a codebook for you to share with your super secret friends.  2 Create your message. Using the code book, write your message carefully and carefully. Please note that pairing your code with a cipher will make your message even more secure!
2 Create your message. Using the code book, write your message carefully and carefully. Please note that pairing your code with a cipher will make your message even more secure!  3 Translate your message. When your friends receive the message, they will need to use their copy of the codebook to translate the message. Make sure they know that you are using a dual method of protection.
3 Translate your message. When your friends receive the message, they will need to use their copy of the codebook to translate the message. Make sure they know that you are using a dual method of protection.
Code book
 1 Select a book. When using a codebook, you will create a code to indicate where the words you want to use in the book. If you want to increase the chances that any of the words you need will be in the code book, then use dictionaries or large travel reference books. You want the number of words used in the book to be large and relate to different topics.
1 Select a book. When using a codebook, you will create a code to indicate where the words you want to use in the book. If you want to increase the chances that any of the words you need will be in the code book, then use dictionaries or large travel reference books. You want the number of words used in the book to be large and relate to different topics.  2 Translate the words of your message into numbers. Take the first word of your message and find it somewhere in the book. Then write down the page number, line number, and word number. Write them together to replace the word you want. Do this operation for each word. You can also use this technique to encrypt phrases if your codebook can provide you with the desired phrase ready-made.
2 Translate the words of your message into numbers. Take the first word of your message and find it somewhere in the book. Then write down the page number, line number, and word number. Write them together to replace the word you want. Do this operation for each word. You can also use this technique to encrypt phrases if your codebook can provide you with the desired phrase ready-made. - So, for example, the word on page 105, the fifth line down, the twelfth in a row would become 105512, 1055.12, or something similar.
 3 Pass the message. Give the encrypted message to your friend. Tom will need to use the same book to reverse translate the message.
3 Pass the message. Give the encrypted message to your friend. Tom will need to use the same book to reverse translate the message.
Police coding
 1 Choose the most popular phrases. This type of code works best when you have a set of phrases that you use the most. It can be anything from a simple "He's cute!" to something more serious, like "I can't meet right now."
1 Choose the most popular phrases. This type of code works best when you have a set of phrases that you use the most. It can be anything from a simple "He's cute!" to something more serious, like "I can't meet right now."  2 Prepare a code for each of the phrases. You can use an analogue of police coding and assign each phrase a number or several letters, or use other phrases (as is done in hospitals). For example, you can say "1099" instead of "This line is bugged" or you can say "I'm thinking about going fishing this weekend."Using numbers is easier when writing, but using phrases is less suspicious.
2 Prepare a code for each of the phrases. You can use an analogue of police coding and assign each phrase a number or several letters, or use other phrases (as is done in hospitals). For example, you can say "1099" instead of "This line is bugged" or you can say "I'm thinking about going fishing this weekend."Using numbers is easier when writing, but using phrases is less suspicious.  3 Remember the code. This type of encoding works best if you can keep all of the phrases in mind, although it never hurts to have a book of code as a safety net!
3 Remember the code. This type of encoding works best if you can keep all of the phrases in mind, although it never hurts to have a book of code as a safety net!
Method 2 of 3: Ciphers
Date based encryption
 1 Choose a date. For example, it will be Steven Spielberg's birthday on December 18, 1946. Write this date using numbers and forward slashes (12/18/46), then remove the slashes to get the six-digit number 121846, which you can use to transmit the encrypted message.
1 Choose a date. For example, it will be Steven Spielberg's birthday on December 18, 1946. Write this date using numbers and forward slashes (12/18/46), then remove the slashes to get the six-digit number 121846, which you can use to transmit the encrypted message.  2 Assign a number to each letter. Imagine the message "I love Steven Spielberg's films." Below the message, you write your six-digit number over and over until the very end of the sentence: 121 84612184 612184 6121846 121846121.
2 Assign a number to each letter. Imagine the message "I love Steven Spielberg's films." Below the message, you write your six-digit number over and over until the very end of the sentence: 121 84612184 612184 6121846 121846121.  3 Encrypt your message. Write the letters from left to right. Move each letter of the plain text by the number of units indicated below it. The letter “M” is shifted one unit and becomes “H”, the letter “H” is shifted by two units and becomes “P”. Please note that the letter "I" is shifted by 2 units, for this you need to jump to the beginning of the alphabet, and becomes "B". Your final message will be "Npyo hfogbushchg yynyfya chukgmsё tsyuekseb".
3 Encrypt your message. Write the letters from left to right. Move each letter of the plain text by the number of units indicated below it. The letter “M” is shifted one unit and becomes “H”, the letter “H” is shifted by two units and becomes “P”. Please note that the letter "I" is shifted by 2 units, for this you need to jump to the beginning of the alphabet, and becomes "B". Your final message will be "Npyo hfogbushchg yynyfya chukgmsё tsyuekseb".  4 Translate your message. When someone wants to read your message, all they need to know is what date you used for encoding. To transcode, use the reverse process: write the numeric code, then return the letters in the opposite order.
4 Translate your message. When someone wants to read your message, all they need to know is what date you used for encoding. To transcode, use the reverse process: write the numeric code, then return the letters in the opposite order. - Date encoding has the additional advantage that the date can be absolutely anything. You can also change the date at any time. This makes it much easier to update the cipher system than other methods. However, it is best to avoid famous dates such as May 9, 1945.
Encryption with a number
- 1 Choose a secret number with your friend. For example, the number 5.
- 2 Write your message (no spaces) with this number of letters in each line (don't worry if the last line is shorter). For example, the message "My cover is down" would look like this:
- Moepre
- open
- hieras
- covered
- 3 To create a cipher, take the letters from top to bottom and write them down. The message will be "Miikokererrypyatrtao".
- 4 To decipher your message, your friend must count the total number of letters, divide by 5, and determine if there are incomplete lines. Then he / she writes these letters in columns so that there are 5 letters in each row and one incomplete line (if any), and reads the message.
Graphic cipher
 1 Draw the hash and + signs. Create the base of your cipher on a piece of paper. It will look like # and + (rotate the plus sign so it looks like a diamond, not a square).
1 Draw the hash and + signs. Create the base of your cipher on a piece of paper. It will look like # and + (rotate the plus sign so it looks like a diamond, not a square). 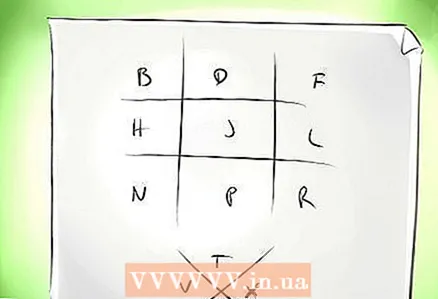 2 Arrange the letters in the cells. These shapes have cells between the lines. Fill in these cells with two letters of the alphabet. Place letters randomly and do not use the same letter twice.
2 Arrange the letters in the cells. These shapes have cells between the lines. Fill in these cells with two letters of the alphabet. Place letters randomly and do not use the same letter twice. - Any addressee of the message will need to have the same copy of the base of the cipher with letters in order to read your message.
 3 Write down your code. Take the first letter of your message. Find it at the base of the cipher. Look at the lines that are around it. Draw the same lines as the lines that form the cells at the base of the cipher. If the letter you are writing is the second in the cell, add a dot to the lines. Repeat this operation for each letter of the message.
3 Write down your code. Take the first letter of your message. Find it at the base of the cipher. Look at the lines that are around it. Draw the same lines as the lines that form the cells at the base of the cipher. If the letter you are writing is the second in the cell, add a dot to the lines. Repeat this operation for each letter of the message.
Caesar's rearrangement
 1 Create your own cipher alphabet. The Caesar cipher moves the alphabet and then replaces the letters with their new number in order. This makes the code harder to crack if you change the constellation regularly. For example, a 3-permutation cipher would mean that A becomes E, B becomes Y, C becomes I, etc. If you want to write "See you tomorrow at the station," then the message will look like "Yaopnvfeviyo eeyapne ke opekuyoyo."
1 Create your own cipher alphabet. The Caesar cipher moves the alphabet and then replaces the letters with their new number in order. This makes the code harder to crack if you change the constellation regularly. For example, a 3-permutation cipher would mean that A becomes E, B becomes Y, C becomes I, etc. If you want to write "See you tomorrow at the station," then the message will look like "Yaopnvfeviyo eeyapne ke opekuyoyo." - There are many options for reordering the alphabet before generating code. This makes the cipher more secure.
 2 Record your message. Having a helper like the decoding circle can make this easier if you can prepare one that suits your code.
2 Record your message. Having a helper like the decoding circle can make this easier if you can prepare one that suits your code.  3 Translate the message. The person decrypting your code only needs to know the number in order to correctly reconstruct the alphabet. Change it regularly, but make sure you can safely communicate what will be the new alphabet shift number.
3 Translate the message. The person decrypting your code only needs to know the number in order to correctly reconstruct the alphabet. Change it regularly, but make sure you can safely communicate what will be the new alphabet shift number.
Method 3 of 3: Secret Languages
Confused language
 1 Identify words that begin with vowels. If there are any, just add "ay" at the end of the word. For example, “ear” will become “ear”, “arch” will become “arkaai” and “insult” will become “insult”.
1 Identify words that begin with vowels. If there are any, just add "ay" at the end of the word. For example, “ear” will become “ear”, “arch” will become “arkaai” and “insult” will become “insult”. 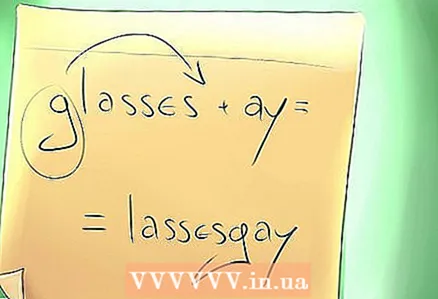 2 Identify words that begin with a consonant. If there are any, then move the first letter of the word to the end and add "ay". If there are two (or more) consonants at the beginning of a word, rearrange them and add "ay".
2 Identify words that begin with a consonant. If there are any, then move the first letter of the word to the end and add "ay". If there are two (or more) consonants at the beginning of a word, rearrange them and add "ay". - For example, “corpse” will become “uptrai”, “gram” will become “ammgray” and “thought” will become “think”.
 3 Speak confused language. Confused language works best if you speak it quickly, but it takes some preparation time. Don't stop practicing!
3 Speak confused language. Confused language works best if you speak it quickly, but it takes some preparation time. Don't stop practicing!
Beep code
 1 Create your sound code. This code will work just like Morse code. You will need to assign a sound rhythm code to each letter or individual word. Choose rhythms that you can remember.
1 Create your sound code. This code will work just like Morse code. You will need to assign a sound rhythm code to each letter or individual word. Choose rhythms that you can remember.  2 Teach your code to others. The code should always be in memory, so teach the code to everyone with whom you plan to use it.
2 Teach your code to others. The code should always be in memory, so teach the code to everyone with whom you plan to use it.  3 Tap your message. Use your fingers, the end of a pencil, or other tool to convey your message. Try to be secretive. You don't need anyone to guess that you are communicating.
3 Tap your message. Use your fingers, the end of a pencil, or other tool to convey your message. Try to be secretive. You don't need anyone to guess that you are communicating.
Gibberish
 1 Learn to speak gibberish. Gibberish is a language game like a confused language, but it sounds more complicated. Short explanation - you need to add "-otag" (or any equivalent) before each vowel in a syllable. This is much more tricky than it really sounds! You will need practice to master this code perfectly.
1 Learn to speak gibberish. Gibberish is a language game like a confused language, but it sounds more complicated. Short explanation - you need to add "-otag" (or any equivalent) before each vowel in a syllable. This is much more tricky than it really sounds! You will need practice to master this code perfectly.
Tips
- Hide your code in a place that only the sender and recipient know about. For example, unscrew any pen and put your code inside it, put the pen back, find a place (such as a pencil holder) and tell the recipient where and type of pen.
- Encrypt spaces as well to confuse your code even more. For example, you can use letters (E, T, A, O, and H work best) instead of spaces. They are called dummies. S, b, b, and Y will look too obvious for experienced code breakers, so do not use them or other prominent characters.
- You can create your own code by randomly rearranging letters in words. "Dij yemn in the park" - "Wait for me in the park."
- Always send codes to agents on your side.
- When using Turkish Irish, you do not need to specifically use "eb" before the consonant. You can use "ie", "br", "from" or any other inconspicuous combination of letters.
- When using positional encoding, feel free to add, remove, and even rearrange letters from one place to another to make decryption even more difficult. Make sure your partner understands what you are doing, or it will all be meaningless to her / him. You can split the text into parts so that there are three, four or five letters in each, and then swap them.
- For a Caesar swap, you can swap the letters to any number of places you want, forward or backward. Just make sure the permutation rules are the same for every letter.
- Always destroy decrypted messages.
- If you're using your own code, don't make it too complicated for others to figure out. It may be too difficult to decipher, even for you!
- Use Morse code. This is one of the most famous codes, so your interlocutor will quickly understand what it is.
Warnings
- If you write the code inaccurately, it will make the decoding process more difficult for your partner, provided that you do not use variations of codes or ciphers specially designed to confuse the decryptor (with the exception of your partner, of course).
- Confused language is best used for short words. With long words, it's not as effective because the extra letters are much more visible. The same is true when using it in speech.
What do you need
For codes:
- Book or dictionary
- Pencil
- Paper
For ciphers:
- Score for code
- Pencil
- Paper
- Any date