Content
- Steps
- Part 1 of 4: The Basics of Anonymity
- Part 2 of 4: Protecting Personal Information
- Part 3 of 4: Basic Measures to Ensure Online Anonymity
- Part 4 of 4: Advanced Measures
The worries about maintaining anonymity on the Internet are no longer the sole concern of pornography lovers, terrorists and hackers. Compromised personal data can make you a victim of fraudsters who steal personal information, and harm you from other illegal actions of third parties. Some people are preoccupied with keeping them safe from government surveillance or even foreign government surveillance (and for good reason). At the same time, nothing can provide you with 100% anonymity on the Internet, as there is always loopholesthat can be used to identify you, and in various software there are always some security problems.But if you're looking to create a safer environment for yourself in this digital age, you can take basic precautions to help you obscure or disguise your online identity to some extent.
Steps
Part 1 of 4: The Basics of Anonymity
 1 Understand that websites track visitor information to serve targeted ads and social media links. Many sites even make money by serving ads. A large part of them strive to ensure that visitors click on the ads they are interested in, therefore they try to show targeted ads based on the data collected about them (which can be tracked independently or even purchased), reflecting personal interests, which allows you to select more interesting advertisements. There are many methods of collecting this data, including the installation of tracking cookies, tracking the IP address (the address of your computer on the network), the history of visiting pages, the browser used, the operating system installed, the length of stay on a particular site, the sources of referrals to the site, and even page visits. other sites (using all the same cookies). All this is done automatically when you visit sites that collect information, so you don't even notice it.
1 Understand that websites track visitor information to serve targeted ads and social media links. Many sites even make money by serving ads. A large part of them strive to ensure that visitors click on the ads they are interested in, therefore they try to show targeted ads based on the data collected about them (which can be tracked independently or even purchased), reflecting personal interests, which allows you to select more interesting advertisements. There are many methods of collecting this data, including the installation of tracking cookies, tracking the IP address (the address of your computer on the network), the history of visiting pages, the browser used, the operating system installed, the length of stay on a particular site, the sources of referrals to the site, and even page visits. other sites (using all the same cookies). All this is done automatically when you visit sites that collect information, so you don't even notice it.  2 Be aware that the major search engines store your search history. Popular internet search engines including Google, Yandex, Mail, Bing, and Yahoo! store your search queries in conjunction with an IP address (and account, if you are logged in). All information is collected and analyzed to deliver more accurate targeted advertisements and create the most relevant search results.
2 Be aware that the major search engines store your search history. Popular internet search engines including Google, Yandex, Mail, Bing, and Yahoo! store your search queries in conjunction with an IP address (and account, if you are logged in). All information is collected and analyzed to deliver more accurate targeted advertisements and create the most relevant search results.  3 Understand that social media is also tracking your actions. If you are logged into your account in any of the social networks (for example, it can be the VKontakte network, Odnoklassniki, Facebook, Twitter, and so on), then it can track the history of visits to pages directly related to this network, if the sites have plug-ins of this network (for example, buttons "Like", "Share" and the like).
3 Understand that social media is also tracking your actions. If you are logged into your account in any of the social networks (for example, it can be the VKontakte network, Odnoklassniki, Facebook, Twitter, and so on), then it can track the history of visits to pages directly related to this network, if the sites have plug-ins of this network (for example, buttons "Like", "Share" and the like).  4 Be aware that most likely your ISP is also analyzing your traffic to know what you are doing on the network. Most often, this is how the provider checks whether the network is being used to download torrent files or materials protected by copyright.
4 Be aware that most likely your ISP is also analyzing your traffic to know what you are doing on the network. Most often, this is how the provider checks whether the network is being used to download torrent files or materials protected by copyright.  5 Understand that it is impossible to achieve complete anonymity on the web. No matter how carefully you hide, it always remains some information that can potentially be used to track you down and identify you. The purpose of using anonymity tools is to reduce the amount of personal information available to third parties, but due to the very nature of the Internet, complete anonymity cannot be achieved.
5 Understand that it is impossible to achieve complete anonymity on the web. No matter how carefully you hide, it always remains some information that can potentially be used to track you down and identify you. The purpose of using anonymity tools is to reduce the amount of personal information available to third parties, but due to the very nature of the Internet, complete anonymity cannot be achieved.  6 Understand the balance you need. When browsing the Internet, you need to choose between convenience and anonymity. Keeping anonymity online is not easy and requires significant effort and deliberate action. You will experience noticeable slowdowns in your internet connection when you visit websites and will be forced to take additional steps before you even go online. If your anonymity is important to you, be prepared to make certain sacrifices.
6 Understand the balance you need. When browsing the Internet, you need to choose between convenience and anonymity. Keeping anonymity online is not easy and requires significant effort and deliberate action. You will experience noticeable slowdowns in your internet connection when you visit websites and will be forced to take additional steps before you even go online. If your anonymity is important to you, be prepared to make certain sacrifices. - In the next section of the article, we will tell you how to avoid associating personal information with your IP address, but we do not guarantee that you will remain anonymous. To further increase your anonymity, you should also read the last two sections of the article.
Part 2 of 4: Protecting Personal Information
 1 To register on various sites, use a disposable email address or use a postal service that provides anonymity. Make sure that your email account does not contain personal information. For example, email services such as ProtonMail, Tutanota and the like claim to be completely reliable and secure.
1 To register on various sites, use a disposable email address or use a postal service that provides anonymity. Make sure that your email account does not contain personal information. For example, email services such as ProtonMail, Tutanota and the like claim to be completely reliable and secure. - Read here for information on creating a disposable email address.
 2 Use anonymous search engines. Most of the major search engines such as Google, Yandex, Mail, Bing and Yahoo !, track the history of search queries and bind them to an IP address. Use alternative search engines like DuckDuckGo or StartPage.
2 Use anonymous search engines. Most of the major search engines such as Google, Yandex, Mail, Bing and Yahoo !, track the history of search queries and bind them to an IP address. Use alternative search engines like DuckDuckGo or StartPage.  3 Use a password manager to keep your saved passwords protected. If you actively use the Internet for more than a week, it is likely that you will need to create and remember a whole bunch of different passwords. It can be tempting to use the same password or small variations everywhere to make your life easier, but this poses a serious risk to your security. If one of the websites that stores your mailbox and account password information is attacked by a hacker, then all your accounts on other sites will be at risk. A password manager will allow you to securely manage passwords for all sites you visit, as well as create strong and even random passwords for them.
3 Use a password manager to keep your saved passwords protected. If you actively use the Internet for more than a week, it is likely that you will need to create and remember a whole bunch of different passwords. It can be tempting to use the same password or small variations everywhere to make your life easier, but this poses a serious risk to your security. If one of the websites that stores your mailbox and account password information is attacked by a hacker, then all your accounts on other sites will be at risk. A password manager will allow you to securely manage passwords for all sites you visit, as well as create strong and even random passwords for them. - You can find more information on installing a password manager online.
- With a password manager, you don't have to worry about creating easy-to-remember passwords. Instead, you can create strong passwords that are nearly impossible to crack with current technology. For example, the password "Kz2Jh @ ds3a $ gs * F% 7" will be much more secure than the password "NicknameMyDogs1983".
Part 3 of 4: Basic Measures to Ensure Online Anonymity
 1 Learn basic terminology. When it comes to maintaining anonymity on the web, it is easy to get confused in technical terminology. Before diving into the study of information, it is necessary to understand the basic meaning of some of the most common terms.
1 Learn basic terminology. When it comes to maintaining anonymity on the web, it is easy to get confused in technical terminology. Before diving into the study of information, it is necessary to understand the basic meaning of some of the most common terms. - Traffic (as a network term) is the flow of data from one computer to another.
- Server is a remote computer that hosts files and creates connections. All websites are stored on servers that you access through a web browser.
- Encryption is a way to protect data sent over a network using a randomly generated code. The encrypted data is encoded with a unique code that only you and the server know about. This ensures that when data is intercepted, it cannot be decrypted.
- Proxy server is a server configured to collect and redirect network traffic. Basically, it allows the user to connect to it, after which the server itself redirects requests to sites. When receiving data from websites, the server will redirect it to you. This is useful for masking your IP address when visiting various sites.
- VPN is a virtual private network protocol. It allows you to secure an encrypted connection between you and the server. VPNs are traditionally used in corporate networks to enable remote workers to securely connect to company information resources. VPN can be imagined as a kind of "tunnel" over the Internet, which allows you to connect directly to the server.
 2 Use a network proxy server. There are thousands of network proxies out there and they change daily. They are websites that route traffic through their own proxy server. They only affect traffic that goes directly through their website. If you just open a new tab in your browser and just start surfing the web, you will lose your anonymity.
2 Use a network proxy server. There are thousands of network proxies out there and they change daily. They are websites that route traffic through their own proxy server. They only affect traffic that goes directly through their website. If you just open a new tab in your browser and just start surfing the web, you will lose your anonymity. - When using network proxy servers, avoid visiting sites that ask for passwords (for example, social networks, banks, etc.), as proxy servers can never be trusted and they can steal your account and banking information.
- In most cases, network proxies are unable to display certain content, such as video.
 3 Connect to a real proxy server. A proxy server is a server that relays your internet traffic. It is useful for masking your private IP address from websites when you connect through a proxy. However, you will have to trust the proxy server and hope that it will not do malicious actions with your traffic.
3 Connect to a real proxy server. A proxy server is a server that relays your internet traffic. It is useful for masking your private IP address from websites when you connect through a proxy. However, you will have to trust the proxy server and hope that it will not do malicious actions with your traffic. - On the Internet, you can find information about a wide variety of proxy servers, both free and paid. Free servers usually generate revenue through advertising.
- Once you find the proxy server you want to connect to, you need to configure your browser accordingly to establish a connection. This will only affect the traffic of a specific browser (for example, messengers will not send information through a proxy if they are not configured as well).
- By analogy with network proxy servers, you should avoid entering passwords and important information, since you cannot completely trust that the organization that provided you with access to the proxy will not disclose your data to third parties.
- Do not connect to "open" proxies. Such proxy servers are open to third parties and are usually used by cybercriminals to carry out illegal activities.
 4 Use or subscribe to a VPN. The VPN will encrypt your outbound and inbound traffic, enhancing security. Also, your traffic will appear as traffic coming from a VPN server, which is similar to using a proxy server. In most cases, VPN is provided for a fee. At the same time, in many cases, traffic is still monitored in accordance with legal requirements.
4 Use or subscribe to a VPN. The VPN will encrypt your outbound and inbound traffic, enhancing security. Also, your traffic will appear as traffic coming from a VPN server, which is similar to using a proxy server. In most cases, VPN is provided for a fee. At the same time, in many cases, traffic is still monitored in accordance with legal requirements. - Do not trust a VPN service company that claims to not track any information. No company would risk its very existence to protect one client from the request for information by the competent authorities.
 5 Use the Tor browser. Tor is a network that acts like many proxies, pushing traffic a large number of times before it reaches a particular site or user. Only the traffic that passes through the Tor browser will be anonymous, while the pages in this browser will open significantly slower than when using conventional browsers.
5 Use the Tor browser. Tor is a network that acts like many proxies, pushing traffic a large number of times before it reaches a particular site or user. Only the traffic that passes through the Tor browser will be anonymous, while the pages in this browser will open significantly slower than when using conventional browsers. - Learn more about how to use the Tor browser here.
 6 Install a browser add-on or extension that protects your privacy. If your browser supports third-party add-ons and extensions, you have the option to install useful add-ons. These browsers include Google Chrome, Mozilla Firefox, Safari, Microsoft Edge, and Opera.
6 Install a browser add-on or extension that protects your privacy. If your browser supports third-party add-ons and extensions, you have the option to install useful add-ons. These browsers include Google Chrome, Mozilla Firefox, Safari, Microsoft Edge, and Opera. - HTTPS Everywhere (for Chrome, Firefox, Opera) automatically resorts to using the encrypted HTTPS protocol on those sites that support it.
- Privacy Badger, Ghostery, Disconnect block tracking cookies. Privacy Badger decides which cookies are tracking you, unlike the other two, which rely on a periodically updated database of tracking cookies. All three mentioned addons are available for major browsers: Google Chrome, Mozilla Firefox, Opera.
- Privacy Badger can be used in Google Chrome, Mozilla Firefox, Opera.
- Ghostery can be used on Mozilla Firefox, Google Chrome, Internet Explorer, Microsoft Edge, Opera, Safari, Firefox for Android.
- Disconnect used in Google Chrome, Mozilla Firefox, Opera, Safari.
- NoScript - addon exclusively for Firefoxwhich allows you to block JavaScript on websites. Verified sites can be whitelisted manually if they require JavaScript to function properly. You can also temporarily enable JavaScript on specific sites. More information on this can be found on the net.
Part 4 of 4: Advanced Measures
 1 Strictly follow the recommendations of each item in this section. If you really need anonymity, there are a few things you should take care of before going online. It may seem like a lot of work, but following all the recommended steps is the only way that is guaranteed to provide you with at least some semblance of anonymity on the web.
1 Strictly follow the recommendations of each item in this section. If you really need anonymity, there are a few things you should take care of before going online. It may seem like a lot of work, but following all the recommended steps is the only way that is guaranteed to provide you with at least some semblance of anonymity on the web. - This method will help you configure your personal VPN on your personal overseas VPS.This will be much more secure than signing up for a VPN service, since a third party cannot always be trusted with the security of your data.
 2 Install Linux on your home computer's virtual machine. A lot of services are launched on the computer that connect to the Internet, each of which can compromise your anonymity on the network, and you will not even know about it. Windows OS is especially insecure, as well as Mac OS X, but to a lesser extent. The first step to anonymity is to install Linux on a virtual machine, which is analogous to a full-fledged computer in a computer.
2 Install Linux on your home computer's virtual machine. A lot of services are launched on the computer that connect to the Internet, each of which can compromise your anonymity on the network, and you will not even know about it. Windows OS is especially insecure, as well as Mac OS X, but to a lesser extent. The first step to anonymity is to install Linux on a virtual machine, which is analogous to a full-fledged computer in a computer. - The virtual computer is equipped with a “barrier” that prevents access to the physical computer's data. This is important in order not to leave information about your real computer when you go online anonymously.
- Here you can find instructions on how to install Linux on a virtual machine. It's free, but it will take about an hour of your time.
- TailsOS is one of the most popular Linux distributions focused on privacy. It takes up little space and is fully encrypted.
 3 Find a VPS (Virtual Dedicated Server) host in another country. It will cost you a few dollars a month, but will allow you to surf the Internet anonymously. It is important to subscribe to a VPS in another country so that traffic from the VPS cannot lead to your real IP address.
3 Find a VPS (Virtual Dedicated Server) host in another country. It will cost you a few dollars a month, but will allow you to surf the Internet anonymously. It is important to subscribe to a VPS in another country so that traffic from the VPS cannot lead to your real IP address. - You will be using a VPS to install your personal VPN software. This will allow you to connect to the network through your personal VPN, thereby masking your IP address.
- Choose a VPS that allows you to pay for services using methods that do not reveal your identity, for example, using DarkCoin.
- As soon as you subscribe to a VPS, you will need to install your operating system on this server. To easily set up a personal VPN, install one of the following Linux distributions: Ubuntu, Fedora, CentOS, or Debian.
- Please note that a VPS provider may be forced to disclose your VPN information by court order in case of suspicion of illegal activity related to your VPN. You cannot influence this.
 4 Set up a personal VPN (virtual private network) on the VPS. Your computer will need to be connected to a VPN to access the Internet. From the outside, everything will look as if you are accessing the network from the point where the VPS is located, and not from home, in addition, all incoming and outgoing data from the VPS will be encrypted. This step is a little more complicated than installing a virtual machine. However, it is the most important step, so if anonymity is important to you, be sure to follow it. It is designed specifically for OpenVPN on Ubuntu, one of the most trusted free VPNs.
4 Set up a personal VPN (virtual private network) on the VPS. Your computer will need to be connected to a VPN to access the Internet. From the outside, everything will look as if you are accessing the network from the point where the VPS is located, and not from home, in addition, all incoming and outgoing data from the VPS will be encrypted. This step is a little more complicated than installing a virtual machine. However, it is the most important step, so if anonymity is important to you, be sure to follow it. It is designed specifically for OpenVPN on Ubuntu, one of the most trusted free VPNs. - Log into the operating system on your VPS. This process will depend on the VPS you choose.
- Go to the OpenVPN website and download the appropriate software package. There are many options out there, so be sure to choose one that exactly matches the operating system installed on your VPS. All packages available for download can be found at the following link: openvpn.net/index.php/access-server/download-openvpn-as-sw.html.
- Start a terminal on your VPS and enter dpkg -i openvpnasdebpack.debto install the OpenVPN software you downloaded. But if you are not using Ubuntu or Debian, then the command will be different.
- Enter passwd openvpn and set a new password when prompted to create one. This will be the admin password for your OpenVPN.
- Open a web browser on your VPS and enter the address that is displayed in the terminal. This will allow you to open the OpenVPN control panel. Enter your username there openvpn and the password created earlier. Once you complete the initial login, your VPN is ready to go.
 5 Open a web browser in the virtual machine. You will need access to the OpenVPN Connect Client to download the configuration file, which is required to establish communication with the program.
5 Open a web browser in the virtual machine. You will need access to the OpenVPN Connect Client to download the configuration file, which is required to establish communication with the program. - Enter the same address that you used to access the VPS control panel, but without the address component / admin.
- Log in to your OpenVPN administrator account using the username "openvpn" and the password you created earlier.
- Download the file to the virtual machine client.opvn or client.conf.
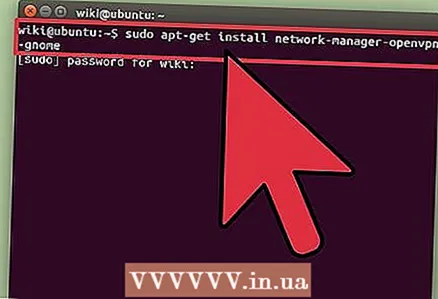 6 Download and install the OpenVPN client on your virtual machine. Once the VPN is configured on your VPS, you will need to configure the virtual machine to communicate directly with it. The instructions below are for Ubuntu and Debian, so you will need to change the appropriate commands if you are using a different OS.
6 Download and install the OpenVPN client on your virtual machine. Once the VPN is configured on your VPS, you will need to configure the virtual machine to communicate directly with it. The instructions below are for Ubuntu and Debian, so you will need to change the appropriate commands if you are using a different OS. - Start a terminal and do the following: sudo apt-get install network-manager-openvpn-gnome
- Wait while the package is downloaded and installed.
- Open Network Manager and click on the VPN tab.
- Click the Import button and then select the config file you downloaded earlier.
- Check your settings. The Certificate and Key fields should be filled in automatically, and your VPN address should reflect the Gateway field.
- Click the IPV4 Settings tab and select Automatic (VPN) addresses only from the Methods drop-down menu. This is guaranteed to redirect all your internet traffic through the VPN.
 7 Download the Tor Browser Bundle to your virtual machine. At this stage, when you have already configured and launched VPS and VPN, you can use the network quite anonymously. The VPN will encrypt all outgoing and incoming traffic from your virtual machine. But if you want to take another step towards anonymity, then the Tor browser will provide additional protection, but at the expense of the speed of access to Internet pages.
7 Download the Tor Browser Bundle to your virtual machine. At this stage, when you have already configured and launched VPS and VPN, you can use the network quite anonymously. The VPN will encrypt all outgoing and incoming traffic from your virtual machine. But if you want to take another step towards anonymity, then the Tor browser will provide additional protection, but at the expense of the speed of access to Internet pages. - You can download the Tor browser from the official website: torproject.org.
- Running Tor over a VPN will hide the fact that you are using Tor from your ISP (it will only see encrypted VPN traffic).
- Run the Tor installer. The default settings provide comprehensive protection for most users.
- For more information on using Tor, click here.
 8 Change your VPS providers regularly. If you are very concerned about security, it is recommended to change VPS providers at least once a month. This means you need to re-configure OpenVPN every time, but gradually with each successive repetition, you will learn how to perform the necessary operations faster and faster. Be sure to completely reconfigure the new VPS before connecting to it.
8 Change your VPS providers regularly. If you are very concerned about security, it is recommended to change VPS providers at least once a month. This means you need to re-configure OpenVPN every time, but gradually with each successive repetition, you will learn how to perform the necessary operations faster and faster. Be sure to completely reconfigure the new VPS before connecting to it.  9 Use the internet wisely. Now that everything is set up, your anonymity relies on your internet habits.
9 Use the internet wisely. Now that everything is set up, your anonymity relies on your internet habits. - Use alternative search engines such as DuckDuckGo or StartPage.
- Avoid sites that use JavaScript. JavaScript can be used to reveal the IP address and de-anonymize your traffic.
- Disconnect from the Internet when opening files downloaded via Tor.
- Do not download torrent files via Tor.
- Avoid any sites that do not use HTTPS (look at the address bar to see if a site is using HTTP or HTTPS).
- Avoid installing browser plugins.