Author:
Laura McKinney
Date Of Creation:
4 August 2021
Update Date:
1 July 2024
Content
- Windows: To view recently opened files, press the key Windows + E to open File Explorer. See the "Recent files" section at the bottom of the main dashboard for signs of an anomaly. You can also view recently opened apps above the Start menu.
- Mac: Click the Apple menu in the top left corner of the screen and select Recent Items (Recent data). You can click Applications (Applications) to view recently used applications, Documents (Documentation) to view files and Servers (Server) to see the list of "outstream" connections.

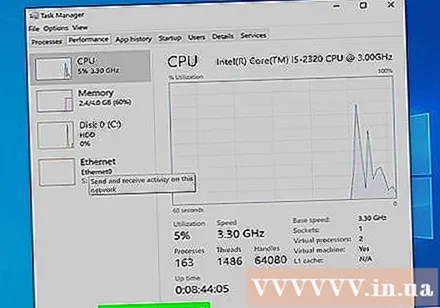
Open Task Manager or Activity Monitor. These utilities can tell you what's going on on your computer.
- Windows - Press Ctrl + Shift + Esc.
- Mac - Open the folder Applications in the Finder, double-click the folder Utilities and double click Activity Monitor.
Erase the entire system if you cannot remove the intrusion. If your computer is still compromised or you think there's still something harmful, the only sure way is to wipe the system clean and reinstall the operating system. However, you need to back up your important data first, as everything will be wiped and reset.
- When backing up data on a infected computer, make sure you scan for each file before backing up. Re-importing old files can always infect your computer again.
- See instructions on how to format a Windows or Mac computer and reinstall the operating system.
Part 2 of 2: Prevent future intrusions
Make sure your firewall has a standard configuration. If you are not using a web server or other program that requires remote access to your computer, you do not need to open the connection ports. Most programs that need a gateway use UPnP - which opens the port when needed and closes itself when the program isn't in use. Opening indefinitely open ports will make your network vulnerable to intrusion.
- Let's see how to set up port forwarding on your router and make sure there are no ports open unless necessary for the server you're using.
Make sure the passwords you use are highly secure and hard to guess. Each password-protected service or program that you use must have a unique password that is hard to guess. This is a way to ensure hackers cannot use the compromised service's password to access other accounts. See the password manager user guide for easier operation.
Avoid using public Wi-Fi spots. Public Wi-Fi spots are risky because you have no control over the network. You don't know if the same Wi-Fi user is controlling the traffic from your computer. Through a public Wi-Fi system, others can access an open web browser or other information. You can reduce the risk by using a VPN every time you connect to Wi-Fi to encrypt your transmission.
- See how to set up the VPN configuration to see how to set up a connection to the VPN service.
Always be wary of programs loaded online. Many "free" programs out there contain other software you don't need. Pay attention to the installation process to make sure you decline any other "invitations". Avoid downloading illegal software, as this is a familiar way of infecting your operating system. advertisement
Advice
- Note that your computer may start automatically to install the update. Many newer computers are set to automatically update the system, usually at night when you are not using the computer. If your computer starts automatically when you are not using it, it is because the computer in Sleep mode is "awakened" to install the updates.
- While your computer can be accessed remotely, the capabilities are usually very low. There are steps you can take to prevent intrusions.