Author:
Gregory Harris
Date Of Creation:
15 August 2021
Update Date:
1 July 2024

Content
- Steps
- Method 1 of 4: Detect and Remove Spyware on Android Device
- Method 2 of 4: Using HijackThis (Windows)
- Method 3 of 4: Using Netstat (Windows)
- Method 4 of 4: Using the Terminal (Mac OS X)
- Tips
- Warnings
Spyware is a type of malicious software (software) that performs certain actions without the user's knowledge, such as displaying advertisements, collecting confidential information, or modifying device settings. If your internet connection slows down, your browser becomes slow, or some other unusual phenomenon occurs, your computer may be infected with spyware.
Steps
Method 1 of 4: Detect and Remove Spyware on Android Device
 1 Remember the signs of spyware. If your internet connection drops frequently or you receive strange text messages, including messages from strangers, on your smartphone, the device is most likely infected with spyware.
1 Remember the signs of spyware. If your internet connection drops frequently or you receive strange text messages, including messages from strangers, on your smartphone, the device is most likely infected with spyware. - Spyware often generates messages with a random set of characters or with a request to enter a specific code.
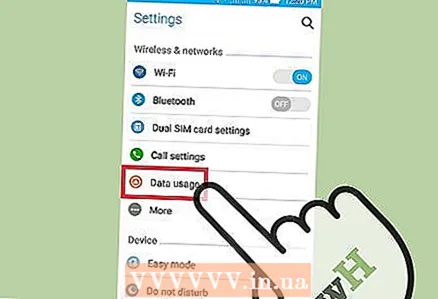 2 Check how apps are using internet traffic. Open the Settings app and click Traffic Control. Scroll down the screen and see what traffic is being consumed by a particular application. As a rule, spyware consumes a lot of traffic.
2 Check how apps are using internet traffic. Open the Settings app and click Traffic Control. Scroll down the screen and see what traffic is being consumed by a particular application. As a rule, spyware consumes a lot of traffic. 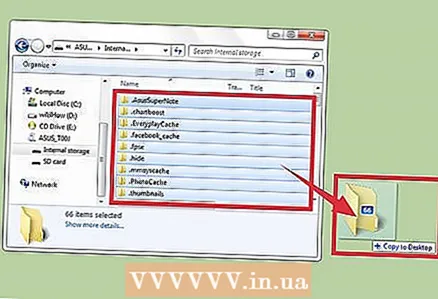 3 Back up your data. Connect your smartphone to your computer using a USB cable, and then drag important files (such as photos or contacts) to your hard drive.
3 Back up your data. Connect your smartphone to your computer using a USB cable, and then drag important files (such as photos or contacts) to your hard drive. - Since the mobile device and the computer are running different operating systems, the computer will not be infected.
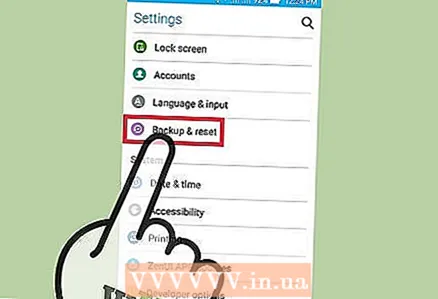 4 Open the Settings app and tap on Backup & Reset. A screen will open with several options, including the option to reset the device to factory settings.
4 Open the Settings app and tap on Backup & Reset. A screen will open with several options, including the option to reset the device to factory settings. 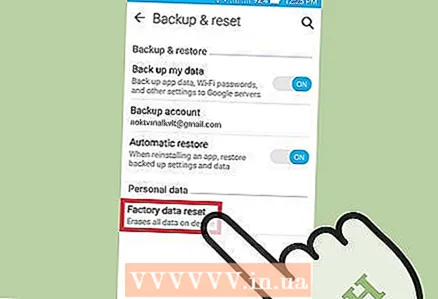 5 Click Reset to Factory Settings. It's at the bottom of the Backup & Reset screen.
5 Click Reset to Factory Settings. It's at the bottom of the Backup & Reset screen. 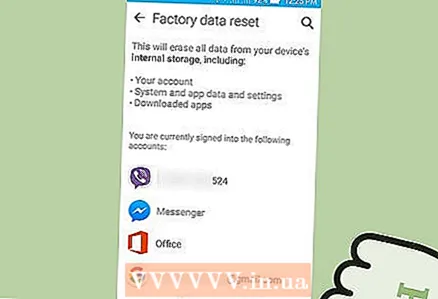 6 Click "Factory data reset". The smartphone will automatically restart and user data and applications, including spyware, will be removed.
6 Click "Factory data reset". The smartphone will automatically restart and user data and applications, including spyware, will be removed. - Please note that resetting to factory settings will erase all user data. Therefore, be sure to back up important information.
Method 2 of 4: Using HijackThis (Windows)
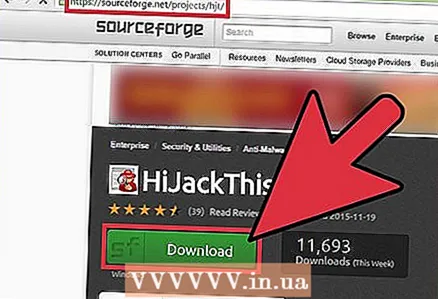 1 Download and install HijackThis. It is a utility that is designed to detect spyware. Double click on the installation file to run it. Once you have installed this utility, run it.
1 Download and install HijackThis. It is a utility that is designed to detect spyware. Double click on the installation file to run it. Once you have installed this utility, run it. - Similar software is Adaware or MalwareBytes.
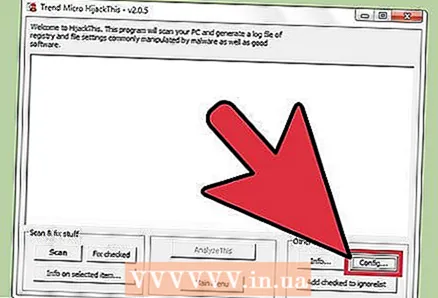 2 Click Config. This button is located in the lower right corner of the screen under the Other Stuff section. The program settings will open.
2 Click Config. This button is located in the lower right corner of the screen under the Other Stuff section. The program settings will open. - In the settings, you can enable or disable certain features, such as file backups. It is recommended that you create a backup if you are working with important files or software. The backup is small; moreover, it can be deleted later (from the folder in which the backups are stored).
- Note that the "Make backups before fixing items" feature is enabled by default.
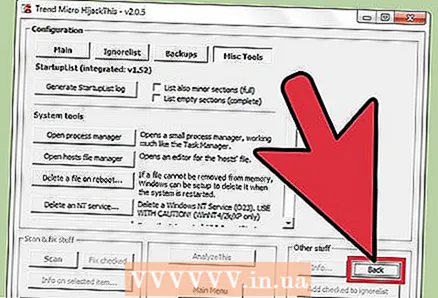 3 Click "Back" to return to the main menu. This button replaces the Config button when the settings window is open.
3 Click "Back" to return to the main menu. This button replaces the Config button when the settings window is open. 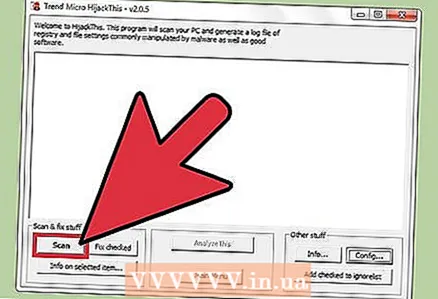 4 Click Scan. This button is located in the lower left corner of the screen, which will display a list of potentially dangerous files. It is important to note that HijackThis will quickly scan the most vulnerable nodes of the system, so not all files in the list will be malicious.
4 Click Scan. This button is located in the lower left corner of the screen, which will display a list of potentially dangerous files. It is important to note that HijackThis will quickly scan the most vulnerable nodes of the system, so not all files in the list will be malicious. 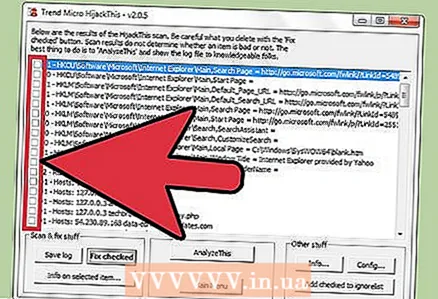 5 Check the box next to the suspicious file and click "Info on selected item". A window will open with detailed information about the file and the reason why it was included in the specified list. After checking the file, close the window.
5 Check the box next to the suspicious file and click "Info on selected item". A window will open with detailed information about the file and the reason why it was included in the specified list. After checking the file, close the window. - The detailed information on the screen displays the location of the file, its possible use and the action that is recommended to be applied to the file.
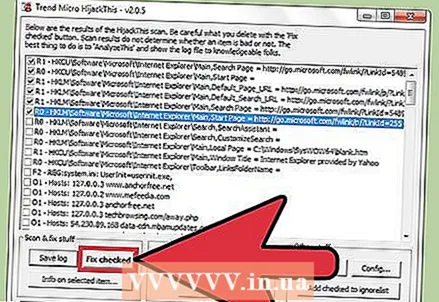 6 Click Fix checked. This button is located in the lower left corner of the screen; HijackThis will either restore or delete the selected file (depending on the selected action).
6 Click Fix checked. This button is located in the lower left corner of the screen; HijackThis will either restore or delete the selected file (depending on the selected action). - You can select multiple files at once; to do this, check the box next to each of them.
- Before performing any action, HijackThis will create (by default) a backup copy of the data so that the user can undo the changes made.
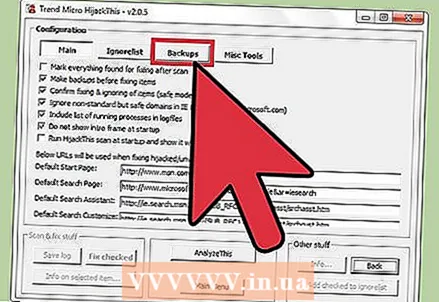 7 Restore data from backup. To undo any changes made by HijackThis, click Config in the lower right corner of the screen and then click Backup. Select the backup file from the list (its name includes the date and time it was created) and then click “Restore”.
7 Restore data from backup. To undo any changes made by HijackThis, click Config in the lower right corner of the screen and then click Backup. Select the backup file from the list (its name includes the date and time it was created) and then click “Restore”. - Backups will be kept until you delete them. That is, you can close HijackThis and restore the data later.
Method 3 of 4: Using Netstat (Windows)
 1 Open a command prompt window. Netstat is a built-in Windows utility that detects spyware and other malicious files. Click on ⊞ Win + Rto open the Run window, and then type cmd... The command line provides interaction with the operating system through text commands.
1 Open a command prompt window. Netstat is a built-in Windows utility that detects spyware and other malicious files. Click on ⊞ Win + Rto open the Run window, and then type cmd... The command line provides interaction with the operating system through text commands. - Use this method if you don't want to install additional software or want more control over the malware removal process.
 2 Enter the command netstat -b and press ↵ Enter. A list of processes that have access to the Internet (may open ports or use an Internet connection) will be displayed.
2 Enter the command netstat -b and press ↵ Enter. A list of processes that have access to the Internet (may open ports or use an Internet connection) will be displayed. - In this command, the operator -b means "binary code". That is, the screen will display the active "binaries" (executable files) and their connections.
 3 Find out which processes are malicious. If you don't know the name of the process, or if it opens a port, it is most likely malware. If you are unsure of any process or port, search for the process name on the Internet. Most likely, other users have already encountered unusual processes and left feedback about their nature (malicious or harmless). If you are sure that the process is malicious, delete the file that starts the process.
3 Find out which processes are malicious. If you don't know the name of the process, or if it opens a port, it is most likely malware. If you are unsure of any process or port, search for the process name on the Internet. Most likely, other users have already encountered unusual processes and left feedback about their nature (malicious or harmless). If you are sure that the process is malicious, delete the file that starts the process. - If you still have not figured out the nature of the process, it is better not to delete the corresponding file, because this can lead to the crash of some program.
 4 Click on Ctrl + Alt + Delete. The Windows Task Manager will open, listing all active processes. Scroll down the list and find the malicious process that you detected using the command line.
4 Click on Ctrl + Alt + Delete. The Windows Task Manager will open, listing all active processes. Scroll down the list and find the malicious process that you detected using the command line. 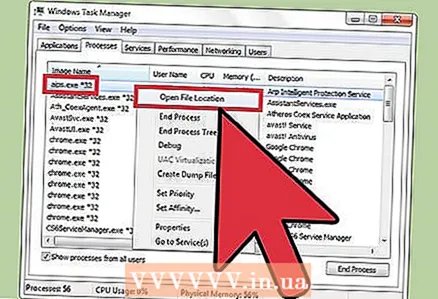 5 Right click on the process name and select "Open file storage location" from the menu. A folder with a malicious file will open.
5 Right click on the process name and select "Open file storage location" from the menu. A folder with a malicious file will open. 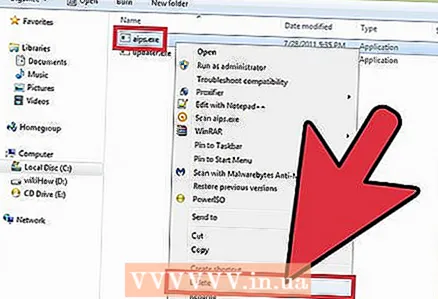 6 Right-click on the file and select "Delete" from the menu. The malicious file will be sent to the Trash, which prevents processes from starting.
6 Right-click on the file and select "Delete" from the menu. The malicious file will be sent to the Trash, which prevents processes from starting. - If a window opens with a warning that the file cannot be deleted because it is in use, return to the Task Manager window, select the process and click End Process. The process will be completed and you can delete the corresponding file.
- If you deleted the wrong file, double-click the Trash to open it, and then drag the file from the Trash to restore it.
 7 Right click on the Trash and select Empty from the menu. This will permanently delete the file.
7 Right click on the Trash and select Empty from the menu. This will permanently delete the file.
Method 4 of 4: Using the Terminal (Mac OS X)
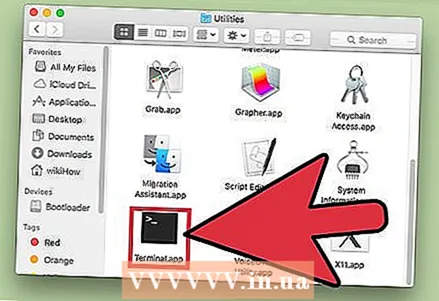 1 Open a terminal. In the terminal, you can run a utility that detects spyware (if, of course, there is one). Click "Applications" - "Utilities" and double click on "Terminal". The terminal provides interaction with the operating system through text commands.
1 Open a terminal. In the terminal, you can run a utility that detects spyware (if, of course, there is one). Click "Applications" - "Utilities" and double click on "Terminal". The terminal provides interaction with the operating system through text commands. - The terminal icon can be found in Launchpad.
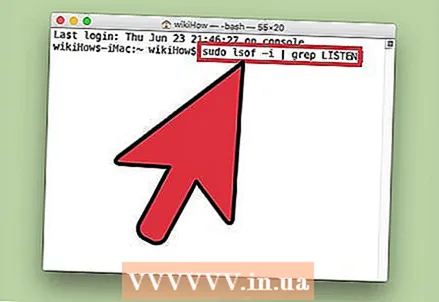 2 Enter the command sudo lsof -i | grep LISTEN and press ⏎ Return. A list of active processes and information about their activity on the network will be displayed.
2 Enter the command sudo lsof -i | grep LISTEN and press ⏎ Return. A list of active processes and information about their activity on the network will be displayed. - Team sudo grants root access to the subsequent command, that is, allows you to view system files.
- lsof is short for "list of open files". That is, this command allows you to view running processes.
- Operator -i indicates that the list of active processes should be accompanied by information about their network activity, because spyware connects to the Internet to communicate with external sources.
- grep LISTEN - this command selects processes that open certain ports (this is how spyware works).
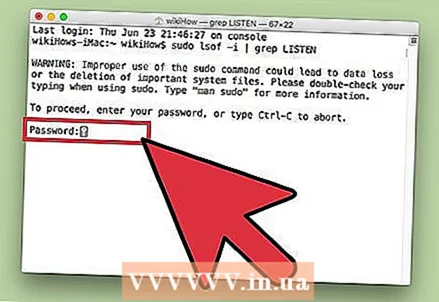 3 Enter your admin password and click ⏎ Return. This is required by the command sudo... Keep in mind that while entering the password, it is not displayed in the terminal.
3 Enter your admin password and click ⏎ Return. This is required by the command sudo... Keep in mind that while entering the password, it is not displayed in the terminal.  4 Find out which processes are malicious. If you don't know the name of the process, or if it opens a port, it is most likely malware. If you are unsure of any process or port, search for the process name on the Internet. Most likely, other users have already encountered unusual processes and left feedback about their nature (malicious or harmless). If you are sure that the process is malicious, delete the file that starts the process.
4 Find out which processes are malicious. If you don't know the name of the process, or if it opens a port, it is most likely malware. If you are unsure of any process or port, search for the process name on the Internet. Most likely, other users have already encountered unusual processes and left feedback about their nature (malicious or harmless). If you are sure that the process is malicious, delete the file that starts the process. - If you still have not figured out the nature of the process, it is better not to delete the corresponding file, because this can lead to the crash of some program.
 5 Enter the command lsof | grep cwd and press ⏎ Return. The paths to the folders with files corresponding to the active processes will be displayed. Find the malicious process in the list and copy the path to it.
5 Enter the command lsof | grep cwd and press ⏎ Return. The paths to the folders with files corresponding to the active processes will be displayed. Find the malicious process in the list and copy the path to it. - cwd denotes the current working directory.
- To make the lists easier to read, run the last command in a new terminal window; to do this, in the terminal press ⌘ Cmd + N.
 6 Enter sudo rm -rf [path to file] and press ⏎ Return. Insert the file path in brackets. This command will delete the corresponding file.
6 Enter sudo rm -rf [path to file] and press ⏎ Return. Insert the file path in brackets. This command will delete the corresponding file. - rm Is an abbreviation for “remove”.
- Make sure you want to delete this particular file. Remember that the file will be deleted permanently. Therefore, we recommend that you create a backup beforehand. Open the Apple menu and click System Preferences> Time Machine> Backup.
Tips
- If HijackThis produces too many suspicious files, click Save Log to create a text file with the results and post them to this forum. Perhaps other users can recommend what to do with this or that file.
- Ports 80 and 443 are used by many reliable network access programs. Of course, spyware can use these ports, but this is unlikely, meaning the spyware will open other ports.
- When you find and remove spyware, change the passwords for each account you log into from your computer. Better to be safe than sorry.
- Some mobile apps that supposedly detect and remove spyware on Android devices are in fact unreliable or even fraudulent. The best way to clean your smartphone from spyware is to return to factory settings.
- Factory reset is also an effective way to remove spyware on iPhone, but if you don't have root access to system files, chances are the spyware won't be able to infiltrate iOS.
Warnings
- Be careful when deleting unfamiliar files. Deleting a file from the System folder (in Windows) can damage the operating system and then reinstall Windows.
- Likewise, be careful when deleting files using the terminal in Mac OS X. If you think you have found a malicious process, first read the information about it on the Internet.