Author:
Louise Ward
Date Of Creation:
12 February 2021
Update Date:
1 July 2024
Content
If you're connecting to another computer over the network, you probably want to keep your data safe. And SSH is a viable option. To do that, you need to properly set up SSH on your computer and then create an encrypted connection to the server. At the same time, SSH needs to be enabled at both ends of the connection. Follow the instructions below to ensure the security of your connection.
Steps
Part 1 of 3: Connecting for the first time
SSH installation. For Windows, you need to download and install the SSH client. The most famous is Cygwin: you can download the program for free from the developer's website. Download and install as you would any other program. Besides Cygwin, PuTTY is also a popular free option.
- During the Cygwin installation process, you must choose to install OpenSSH from the Net section.
- Linux and Mac OS X have SSH built-in. This is because SSH is a UNIX system and Linux as well as OS X were developed from this system.
- If you are using Windows 10 with the Anniversary Update, you can install Windows Subsystem for Linux: with this feature, SSH will be pre-installed.

Run SSH. Open the terminal program installed by Cygwin, or Bash on Ubuntu on Windows 10, or Terminal on OS X and Linux. SSH uses a terminal interface to interact with other computers. SSH has no graphical interface, so you will have to get used to typing commands.
Checking connection. Before you begin creating your security key and transferring files, you should make sure that SSH is configured correctly on the computer you are using and the other terminal. Enter the following command, instead
by your username on the other computer and by the address of that server or computer: $ ssh@ - When the connection is established, you will be asked to enter a password. As you type, the mouse pointer will not move and any entered characters will not be displayed.
- If there is an error in this step, then SSH is misconfigured on your computer or the computer on the other end does not accept SSH connections.
Part 2 of 3: Learning the basics
Navigate the SSH shell (command interpreter). When connecting to the other end computer for the first time, you should "close" in the HOME directory. To navigate through directory structure, use commandsCD:cd .. moves out to the directory directly in front of the treeCDmove to any specific directory. cd / home / directory / path / move to a specific directory from the home directory.cd ~ return to your HOME directory.
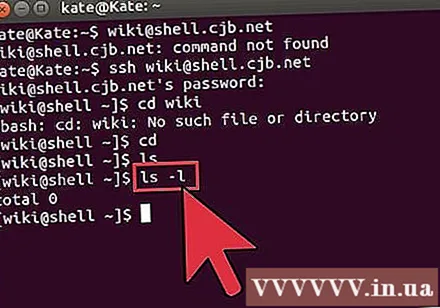
Check the contents of the current directory. To view files and folders in the current directory, you can use the commandls:ls lists all directories and files in the current directory.ls -l lists content in the directory with additional information such as size, permissions, and date.ls-a lists all content, including hidden files and folders.
Copy files from your location to the other computer. To copy files from the current computer to the computer you are accessing remotely, you can use the command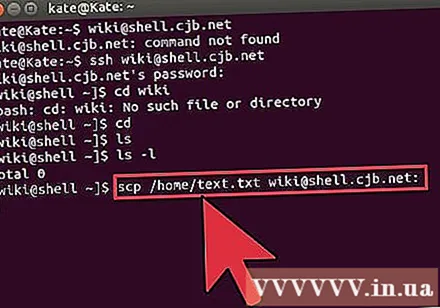
scp:scp / ministry / directory1.txt@ :<đường_dẫn> will copy example_1.txt to <đường_dẫn> specific on the computer that is being accessed remotely. You can leave the field blank <đường_dẫn> to copy to the root of this computer. scp@ : /home/example_1.txt./ will move example_1.txt from the home directory on the remote computer to the directory you are entering directly on this terminal.
Copy files through the shell. You can use commands
cp to copy files in the same directory or to predefined directory:cp example_1.txt example_2.txt will make a copy of example_1.txt and name it example_2.txt right in the current directory.cp example_1.txt directory / will make a copy of example_1 in the directory specified by the directory.
Convert and rename files. If you want to rename or move (without copying) a file, you can use the command
mv:mv example_1.txt example_2.txt will rename example_1.txt to example_2.txt, the file will remain in the old directory.folder_1 directory2 rename directory_1 to directory2. Content contained in the directory remains the same.mv directory_1.txt directory_1 / move example_1.txt to directory_1.mv directory_1.txt directory_1 / example_2.txt move example_1.txt to directory_1 and rename it to directory_2.txt.
Delete files and folders. To delete content on a computer that is being accessed remotely, you can use a command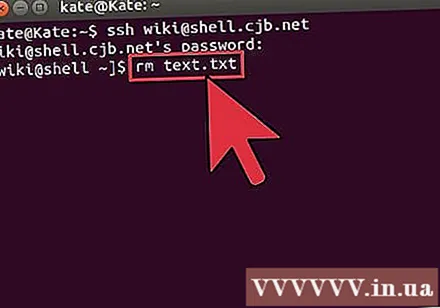
rm:rm example_1.txt delete the file example_1.txt name.rm –I example_1.txt deletes example_1.txt file after getting confirmation from you.rm directory_1 / delete directory_1 with all contents.
Change permissions of files. You can change the read and write permissions of files with the command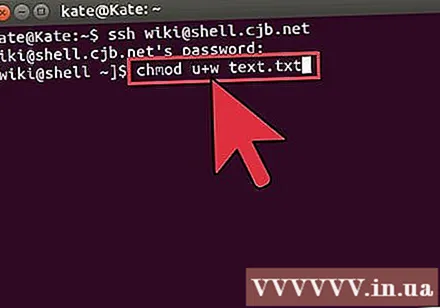
chmod:chmod u + w example_1.txt adds write (edit) permission to user (u). You can also use pluginsg is for group rights ando gives universal rights.chmod g + r example_1.txt adds read (access) permissions to the group file.- The list of commands that you can use to secure or open various aspects of your machine is quite lengthy.
Learn other basic haphazard commands. There are still a few more important commands that are used quite a lot on the shell interface, including: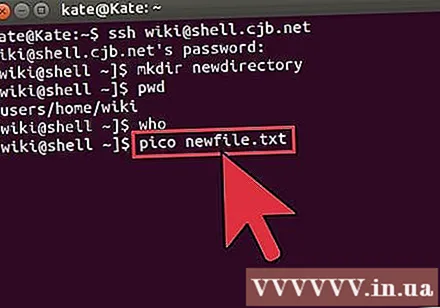
new directory mkdir creates a subdirectory called the new directory.pwd shows the current directory location.who shows who is currently logged into the system.pico newfile.txt oren newfile.txt creates a new file and opens the file editor. Different machines may have different file editors installed. Pico and vi are the two most popular. If your computer uses a different file editor, you may have to use different commands.
Get detailed information about any order. If you are not sure what the command does, you can use the command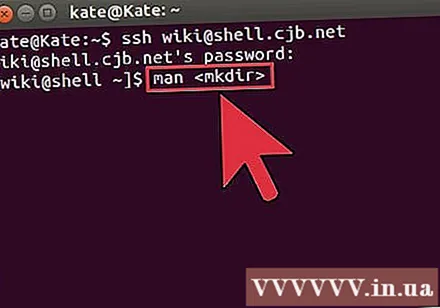
man to learn about all possible parameters and uses:mandisplays information about that command man -kfind every command page for the specified keyword.
Part 3 of 3: Generating encrypted keys
Generate your SSH key. These keys allow you to connect to the remote device without having to enter the password every time you connect. This way is much more secure because with it, you do not need to send a password over the network.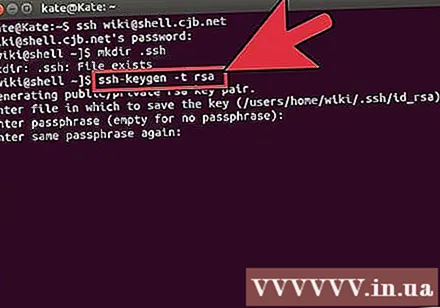
- Create a lock folder on your computer by entering a command
$ mkdir.ssh - Generate public and private keys using commands
$ ssh-keygen -t rsa - You will be asked if you want to create a password for the key: it's optional. If you don't want to create a password, just press Enter. The keys id_rsa and id_rsa.pub will be generated in the.ssh directory.
- Change private key permissions. To make sure that only the private key is readable by you, enter a command
$ chmod 600.ssh / id_rsa
- Create a lock folder on your computer by entering a command
Leave the public key on the other computer. Once the key is generated, you're ready to place the public key on top of the other connection so you can connect without a password. Enter the following command, replace the necessary parts as shown: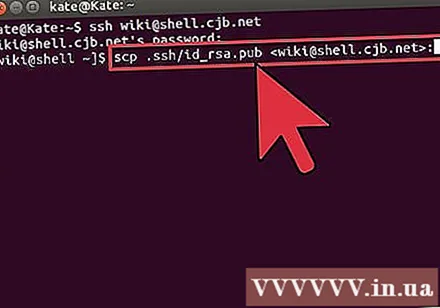
$ scp.ssh / id_rsa.pub@ : - Don't forget the colon (:) at the end of the command.
- You will be asked to enter your password before you start the file transfer.
Install the public key on the other computer. Once placed, you need to install the lock on the other device for it to function properly. First, log on to the other end computer in the same way that you did in step 3.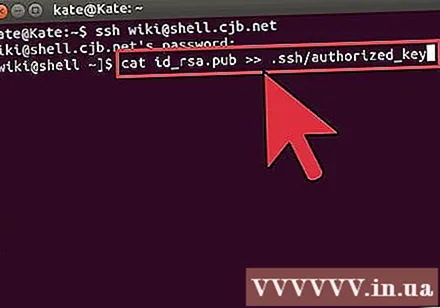
- Create an SSH directory if it does not already exist on this computer:
$ mkdir.ssh - Associate your key with the licensed key file. If this file does not already exist, it will be initialized:
$ cat id_rsa.pub >>. ssh / authorized_keys - Change the permission for the SSH directory to allow access:
$ chmod 700.ssh
- Create an SSH directory if it does not already exist on this computer:
Check if the connection is working or not. After you have installed the key on the computer at the other end of the connection, you should be able to create the connection without having to enter a password. Use the following command to check your connection: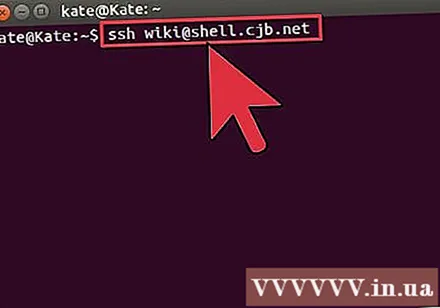
$ ssh@ - If you do not have to enter a password while connecting, the key must have been configured correctly.



