Author:
Roger Morrison
Date Of Creation:
28 September 2021
Update Date:
15 June 2024

Content
- To step
- Method 1 of 4: Install a keylogger
- Method 2 of 4: Using effective ways to guess a password
- Method 3 of 4: Access a password manager
- Method 4 of 4: Recover a password using the appropriate links
- Tips
- Warnings
In this wikiHow article, you can learn how to retrieve the password of a system or account that you do not have access to in principle. This can be useful when, for example, you have problems with one of your children or with an employee and need his or her personal information.
To step
Method 1 of 4: Install a keylogger
 Look for a so-called keylogger program. You can do this by typing the word "keylogger" into a search engine and viewing the search results. A keylogger is a hidden program that runs in the background of a computer's operating system. The program records every key that the user of the computer types, so that you eventually have a record of all passwords and usernames that are typed in when the user visits the associated websites.
Look for a so-called keylogger program. You can do this by typing the word "keylogger" into a search engine and viewing the search results. A keylogger is a hidden program that runs in the background of a computer's operating system. The program records every key that the user of the computer types, so that you eventually have a record of all passwords and usernames that are typed in when the user visits the associated websites.  Choose a reliable keylogger program. Both Best Free Keylogger and Revealer Keylogger Free are safe options if you don't know where to start.
Choose a reliable keylogger program. Both Best Free Keylogger and Revealer Keylogger Free are safe options if you don't know where to start. - Before installing the software, try to determine if the website is legitimate.
- For around € 100 you can buy a keylogger that has undergone a critical check.
 Install your chosen keylogger. If possible, download the program directly to the computer using the password you want to retrieve. If you are using a paid version of the program, instead of a free keylogger, please enter your payment information.
Install your chosen keylogger. If possible, download the program directly to the computer using the password you want to retrieve. If you are using a paid version of the program, instead of a free keylogger, please enter your payment information. - If possible, do this using Paypal.
- If you don't install the keylogger directly on the computer you want to use the program on, you will eventually have to copy it to that computer using a USB stick.
 Install the keylogger. To do this, click twice on the keylogger installation file setup file and follow the on-screen instructions. More than with other programs, it is very important that you carefully read the details of how to use the software and the license agreement shown in the keylogger installation window. You have to be careful not to accidentally consent to the content of your keylogger being distributed on the internet (or with anything else you wouldn't want).
Install the keylogger. To do this, click twice on the keylogger installation file setup file and follow the on-screen instructions. More than with other programs, it is very important that you carefully read the details of how to use the software and the license agreement shown in the keylogger installation window. You have to be careful not to accidentally consent to the content of your keylogger being distributed on the internet (or with anything else you wouldn't want).  Activate the keylogger. Once the program is running, you often have the option of making it "invisible". If you can, hide the program from view and let it run in the background.
Activate the keylogger. Once the program is running, you often have the option of making it "invisible". If you can, hide the program from view and let it run in the background.  View the results of the keylogger. Depending on how often the computer in question is used, it is probably best to give it about a week before viewing the results.
View the results of the keylogger. Depending on how often the computer in question is used, it is probably best to give it about a week before viewing the results. - Depending on the keylogger you are using, you may not need to search the data as extensively - some keyloggers keep a list of the names of the websites visited.
- If you install a simple keylogger that simply records the keystrokes, you will have to search the data for recognizable login details (such as a username or a phone number).
Method 2 of 4: Using effective ways to guess a password
 Look for passwords stored on the computer of the owner of the account you want to compromise. If you have access to the physical computer that the owner of the account works from, he or she may have saved the frequently used passwords somewhere in a document.
Look for passwords stored on the computer of the owner of the account you want to compromise. If you have access to the physical computer that the owner of the account works from, he or she may have saved the frequently used passwords somewhere in a document. - Most computers allow you to skim through files within a search bar (PC) or within the search program (Mac). Try entering keywords such as "password", "account" and "username" (or "username").
- Also, don't forget to look for hidden files.
 Write down what you know about the person who created the password. This could be information ranging from his or her date of birth to the name of a favorite pet. The purpose of this is to find possible answers to the person's verification questions, as well as possible candidates for the actual password.
Write down what you know about the person who created the password. This could be information ranging from his or her date of birth to the name of a favorite pet. The purpose of this is to find possible answers to the person's verification questions, as well as possible candidates for the actual password. - For example, the name of his or her favorite pet followed by a number could be a password.
 Use all possible relevant information. If you can't just guess the password and you can't find a file on your computer that is explicitly saved as a password file, try using everything you know about him or her to guess the password. For example, the following information may be helpful:
Use all possible relevant information. If you can't just guess the password and you can't find a file on your computer that is explicitly saved as a password file, try using everything you know about him or her to guess the password. For example, the following information may be helpful: - Personal information (such as the name of his or her favorite pet) - This can help you guess the answers to the control questions. And by typing in the correct answers to the security questions, you can often bypass entering the password.
- Social Media Details - If you are friends with the person on social media (or you know someone who is friends with him or her), you can often find out the answers to the questions he or she likes or dislikes. derive control questions.
 Talk to people who might know the password. Especially if you as a parent want to have access to your child's account, or if you need to investigate a case of fraud for work, chances are that you can talk to certain people who could know something about the password you have. tries to figure it out.
Talk to people who might know the password. Especially if you as a parent want to have access to your child's account, or if you need to investigate a case of fraud for work, chances are that you can talk to certain people who could know something about the password you have. tries to figure it out.
Method 3 of 4: Access a password manager
 Check whether the person who created the password is using a password manager. You can do this by typing "Password Manager" in the search bar of the computer (or in the search program). Password managers store frequently used passwords and use them to access associated systems or pages (such as Facebook or Google). A few common password managers are:
Check whether the person who created the password is using a password manager. You can do this by typing "Password Manager" in the search bar of the computer (or in the search program). Password managers store frequently used passwords and use them to access associated systems or pages (such as Facebook or Google). A few common password managers are: - Keychain
- Google Smart Lock
- Saved browser data
 Open the password manager. Usually the password manager itself is also protected with a password. If you know the password, you can easily view and use all saved passwords to access associated websites or accounts.
Open the password manager. Usually the password manager itself is also protected with a password. If you know the password, you can easily view and use all saved passwords to access associated websites or accounts. - If you do not know the password, you are dependent on the data from the AutoFill function for the website or program you are trying to access.
 Try to enter a username. If the website or account you are trying to access is secured with a password stored in your chosen search engine (or the program you are using), when you type in the username, the password may be automatically saved for you. is filled in.
Try to enter a username. If the website or account you are trying to access is secured with a password stored in your chosen search engine (or the program you are using), when you type in the username, the password may be automatically saved for you. is filled in. - Both Google Chrome and Mozilla do this, as long as the user has the cookies and AutoFill functions enabled.
- If the person who created the password is using a Mac and you have their Keychain password, you may be able to use the Keychain to access their saved passwords. To do this, go to Keychain Access (you should find it in the Utilities folder), open the "Passwords" tab on the left side of the screen and select the appropriate password. After entering the keychain password, you can also display the password as text.
Method 4 of 4: Recover a password using the appropriate links
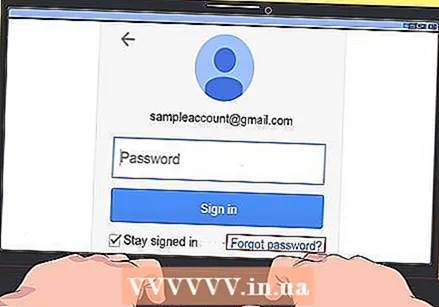 Click on the Forgot password link. You will usually find that link somewhere below (or somewhere else near) the field where you need to enter your "Password".
Click on the Forgot password link. You will usually find that link somewhere below (or somewhere else near) the field where you need to enter your "Password".  Find out what options you have to recover your password. You can usually get your password back in one of the following ways:
Find out what options you have to recover your password. You can usually get your password back in one of the following ways: - By means of a text message to your mobile, containing a link to the password
- Via an email with the password link
- By answering audit questions
 Make sure you have the information you need to recover your password. This is when it is convenient if you know as much as possible about whoever created the password. If that fails, you will need to physically access the phone number or email address of the password creator.
Make sure you have the information you need to recover your password. This is when it is convenient if you know as much as possible about whoever created the password. If that fails, you will need to physically access the phone number or email address of the password creator. - If he or she is using an iOS device that is synced with the computer you are working on, you may be able to see the link to get the password back in the messages from the Mac. This is a risky act, because the person who created the password will also notice that you are changing the password.
 Follow the instructions on the screen. As long as you have everything you need to access the password reset link (or answer the verification questions), you should be able to recover the password and gain access to that account.
Follow the instructions on the screen. As long as you have everything you need to access the password reset link (or answer the verification questions), you should be able to recover the password and gain access to that account.
Tips
- In certain specific situations, stealing someone's password to gain access to that person's data without his or her consent is defensible by law.
Warnings
- Using someone's password to access that person's personal files without his or her permission is a crime.